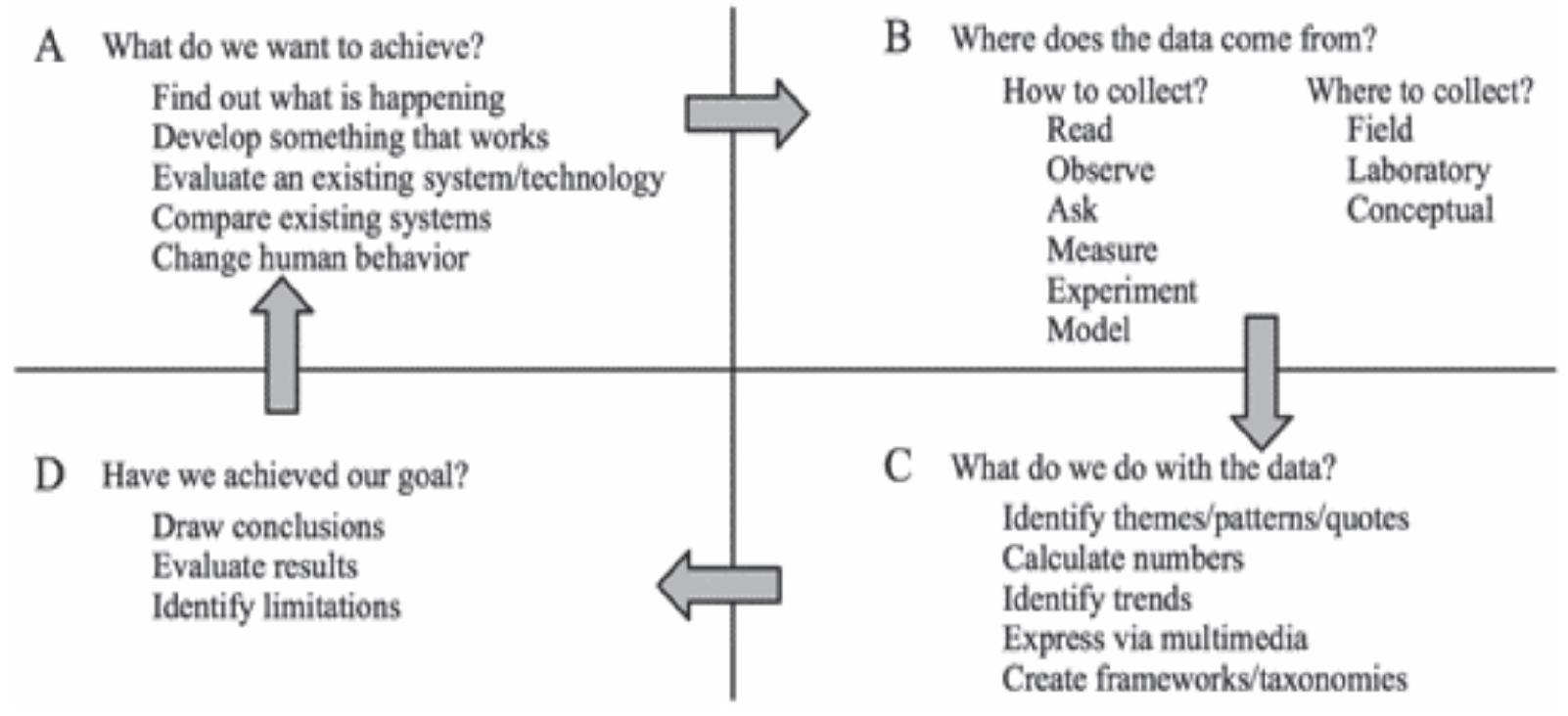
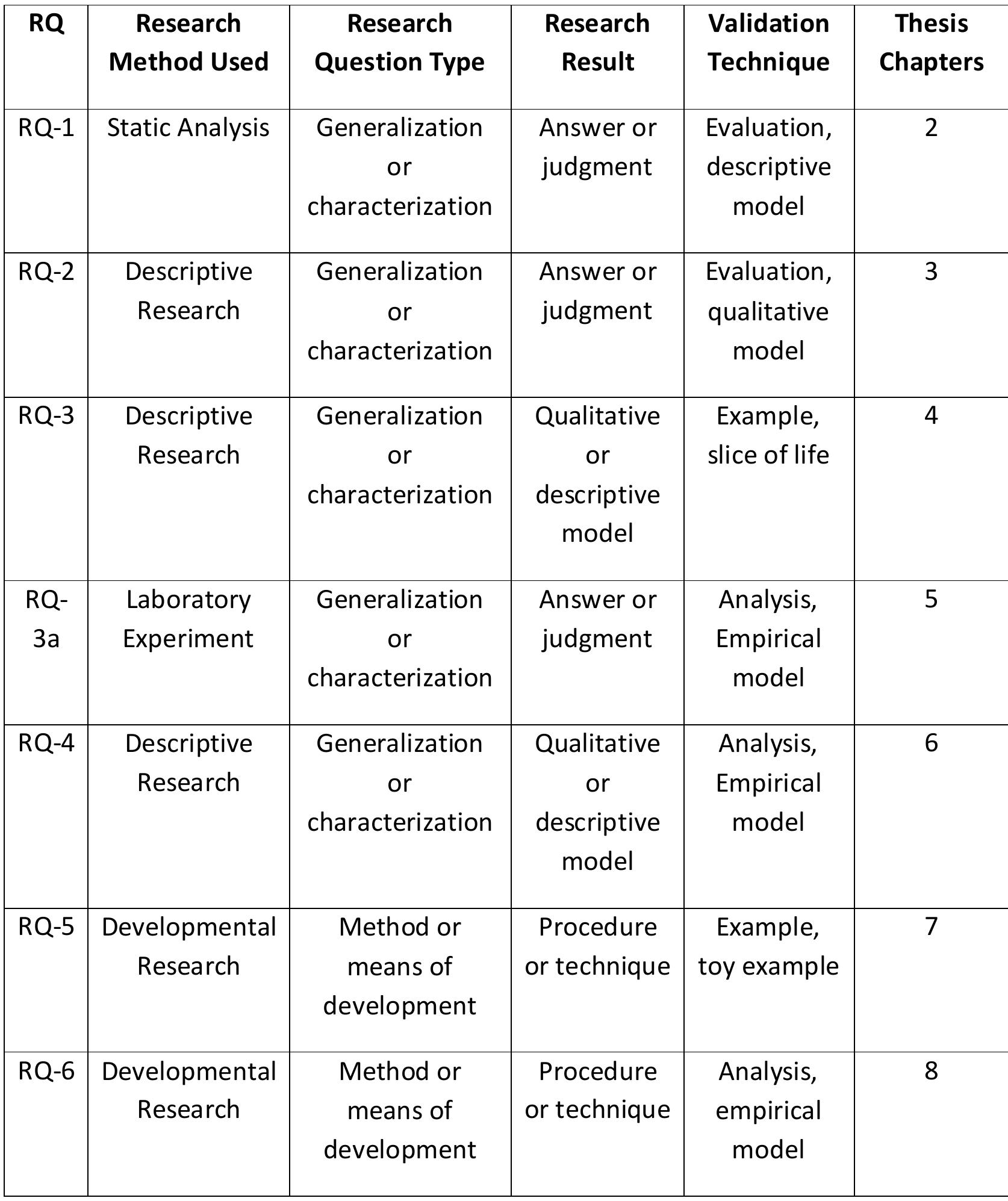
This handbook documents the QUASAR (QUality Assessment of System ARchitectures) method for assessing the quality of the architecture of a software-intensive system. It begins by discussing the challenges that are faced when assessing a... more
In this paper we present the main concepts and principles of a multilevel architecture to help in the development of modularized and reusable software process models under the System Dynamics approach. The conceptual ideas of the... more
This article outlines a reference architecture for social head gaze generation in social robots. The architecture discussed here is grounded in human communication, based on behavioral robotics theory, and captures the commonalities,... more
Definition NUMA is the acronym for Non-Uniform Memory Access. A NUMA cache is a cache memory in which the access time is not uniform but depends on the posi tion of the involved block inside the cache. Among NUMA caches, it... more
Cloud Computing is one of the most pervasive ICT changes of the last few years. Usually, Clouds offer a variety of Services, which are accessible over the Internet. These Services are regulated by some contracts called Service Level... more
Software architecture holds the promise of advancing the state of the art in software engineering. The architecture is emerging as the focal point of many modern reuse/evolutionary paradigms, such as Product Line Engineering, Component... more
As software architecture is becoming an important asset in the development of software systems, the study of quantitative assessment of software architectures is gaining importance due to its role in assessing their quality. Error... more
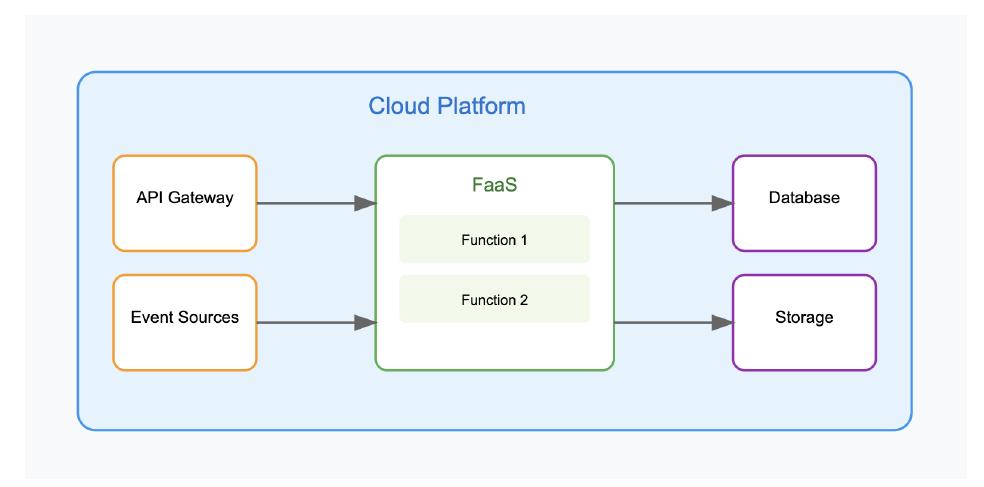
Serverless computing has emerged as a significant paradigm shift in the cloud computing landscape, enabling developers to focus on code without the complexity of managing infrastructure. This paper surveys the various benefits of... more
Recent advances in fields such as Cloud Computing, Web Systems, Internet of Things and Distributed NoSQL DBMS are enabling the development of innovative enterprise information systems that significantly increase the productivity of end... more
Several appealing features of cloud computing such as cost-effectiveness and user-friendliness have made many users and enterprises interested to outsource their sensitive data for sharing via cloud. However, it causes many new challenges... more
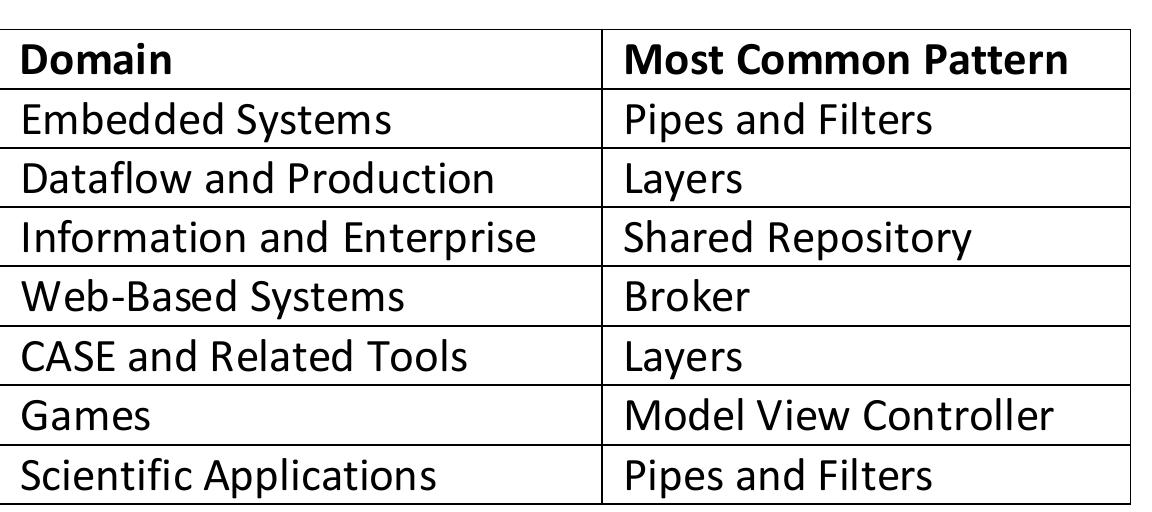
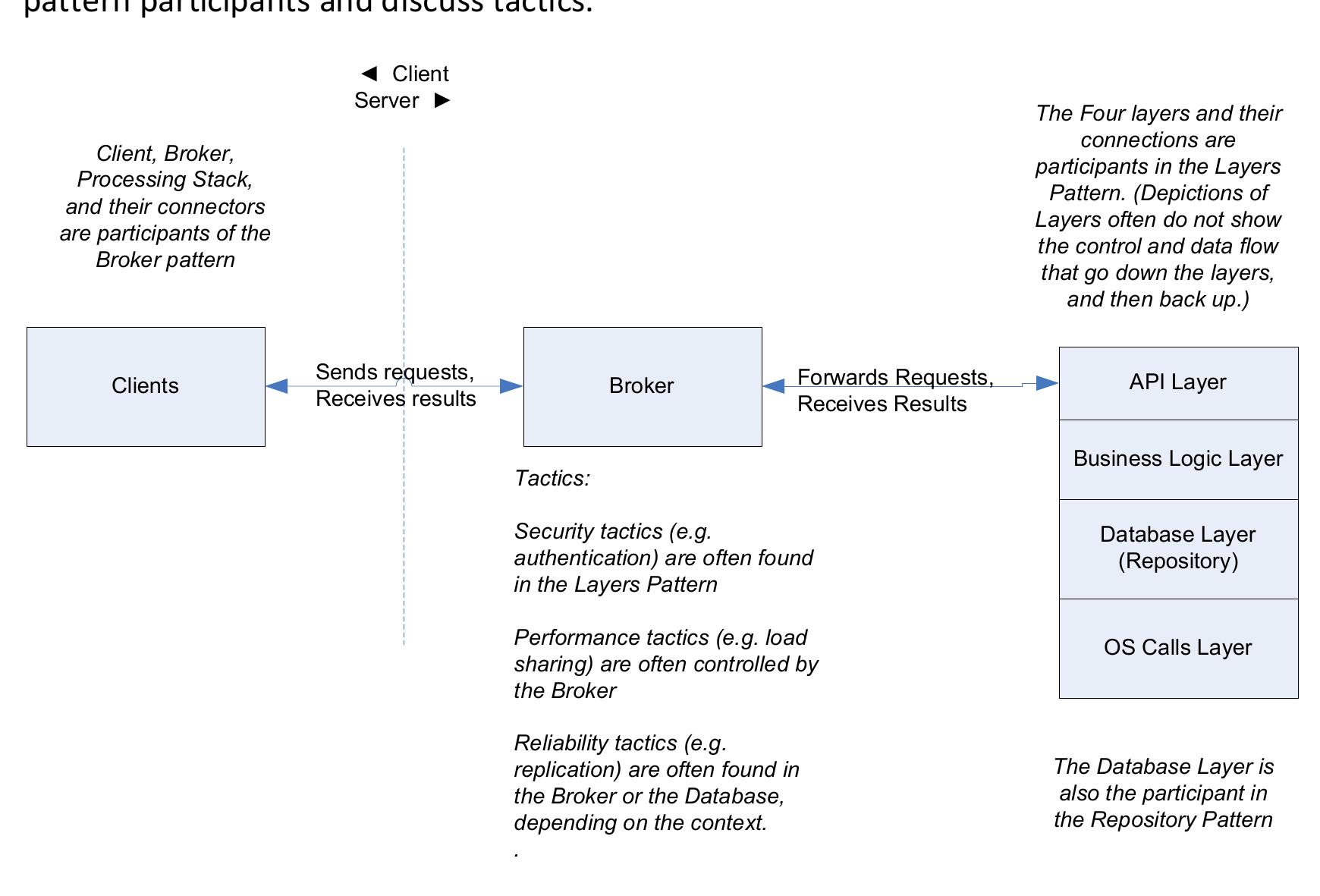
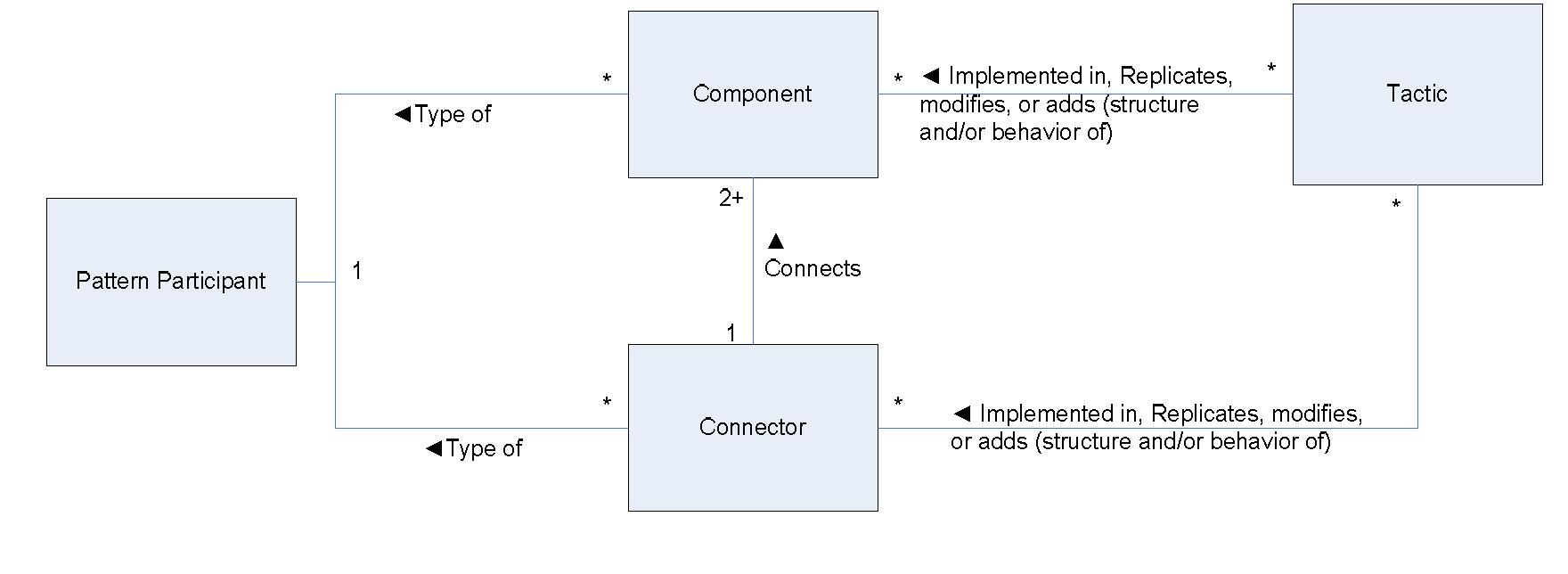
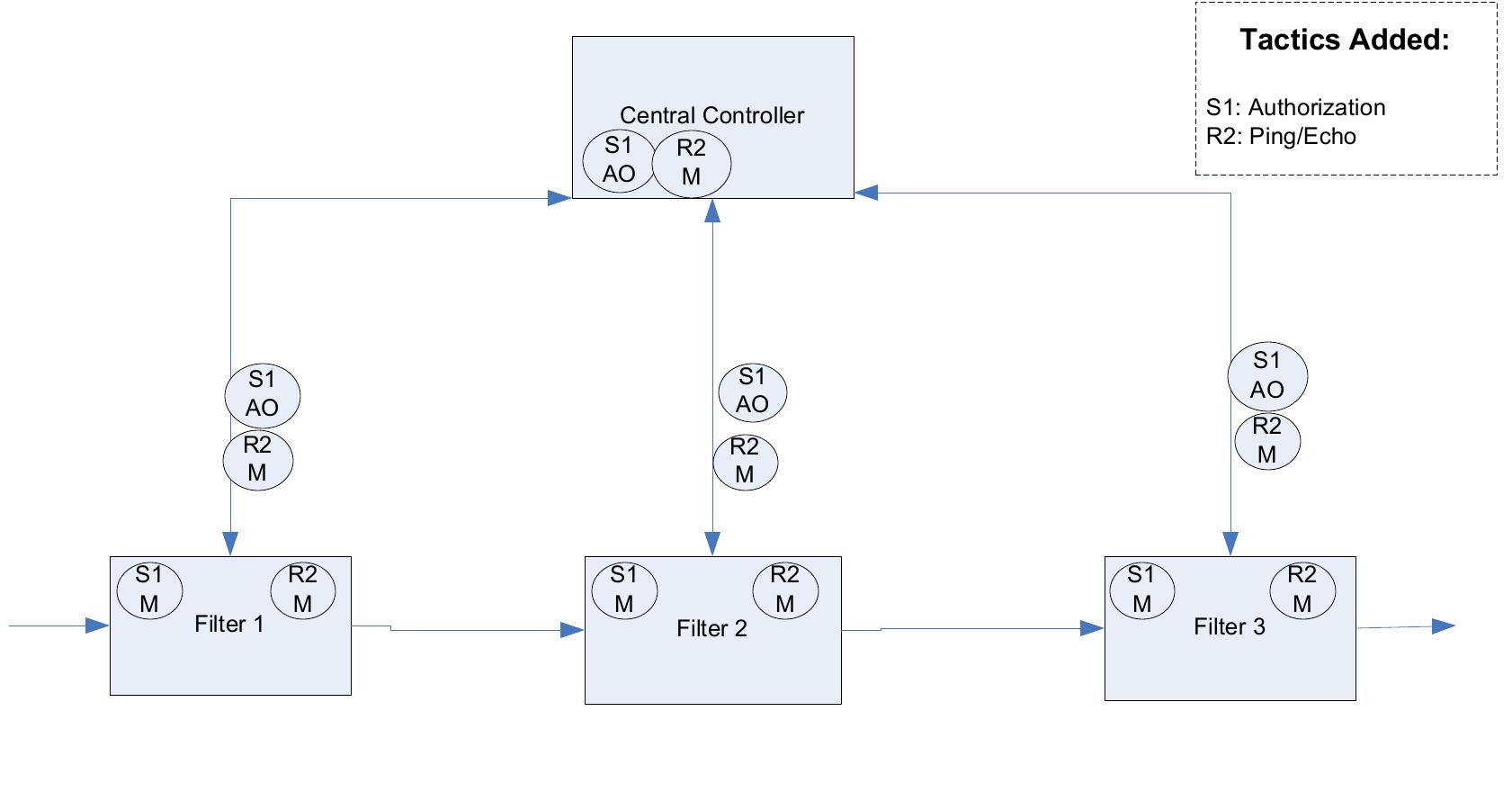
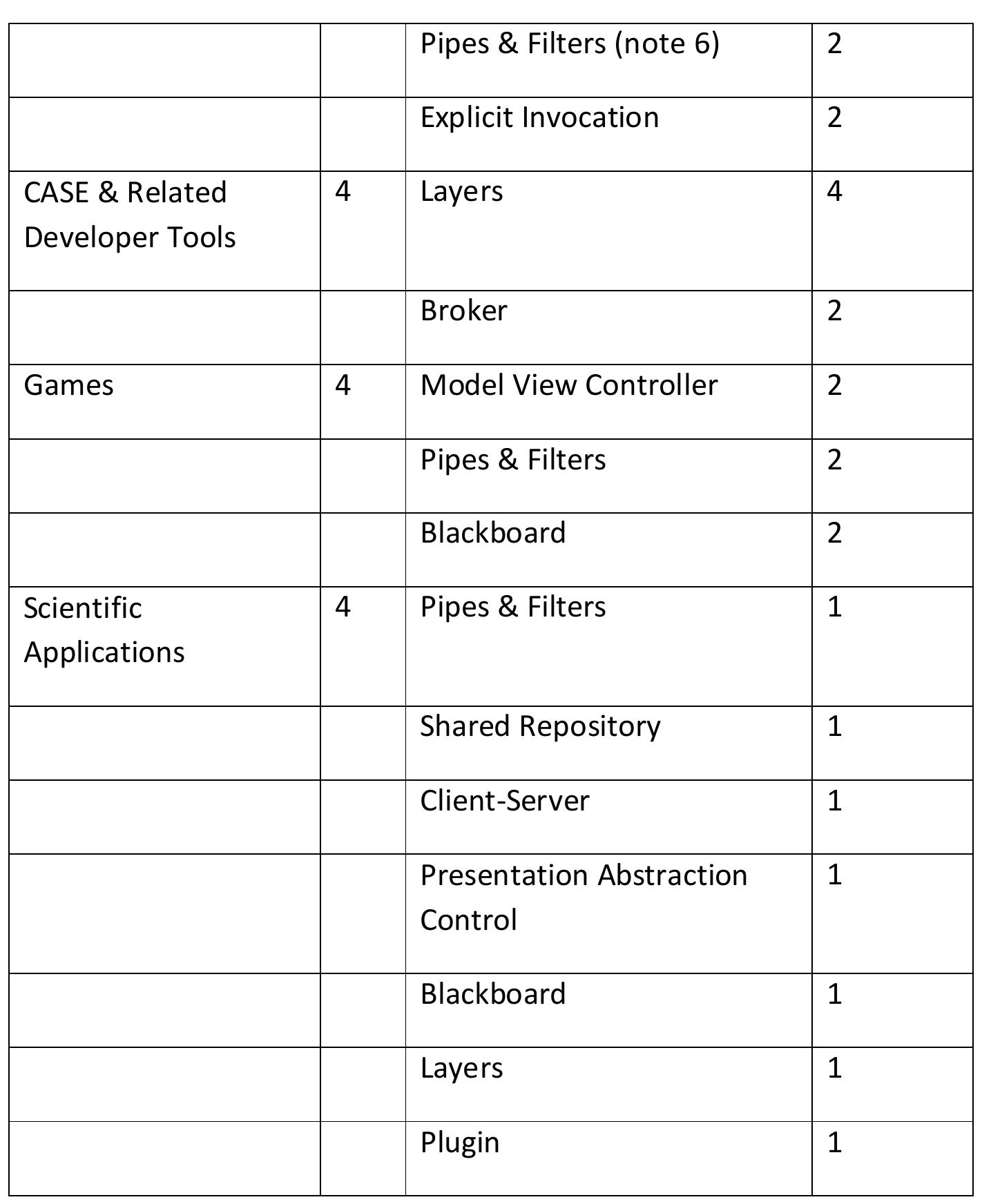
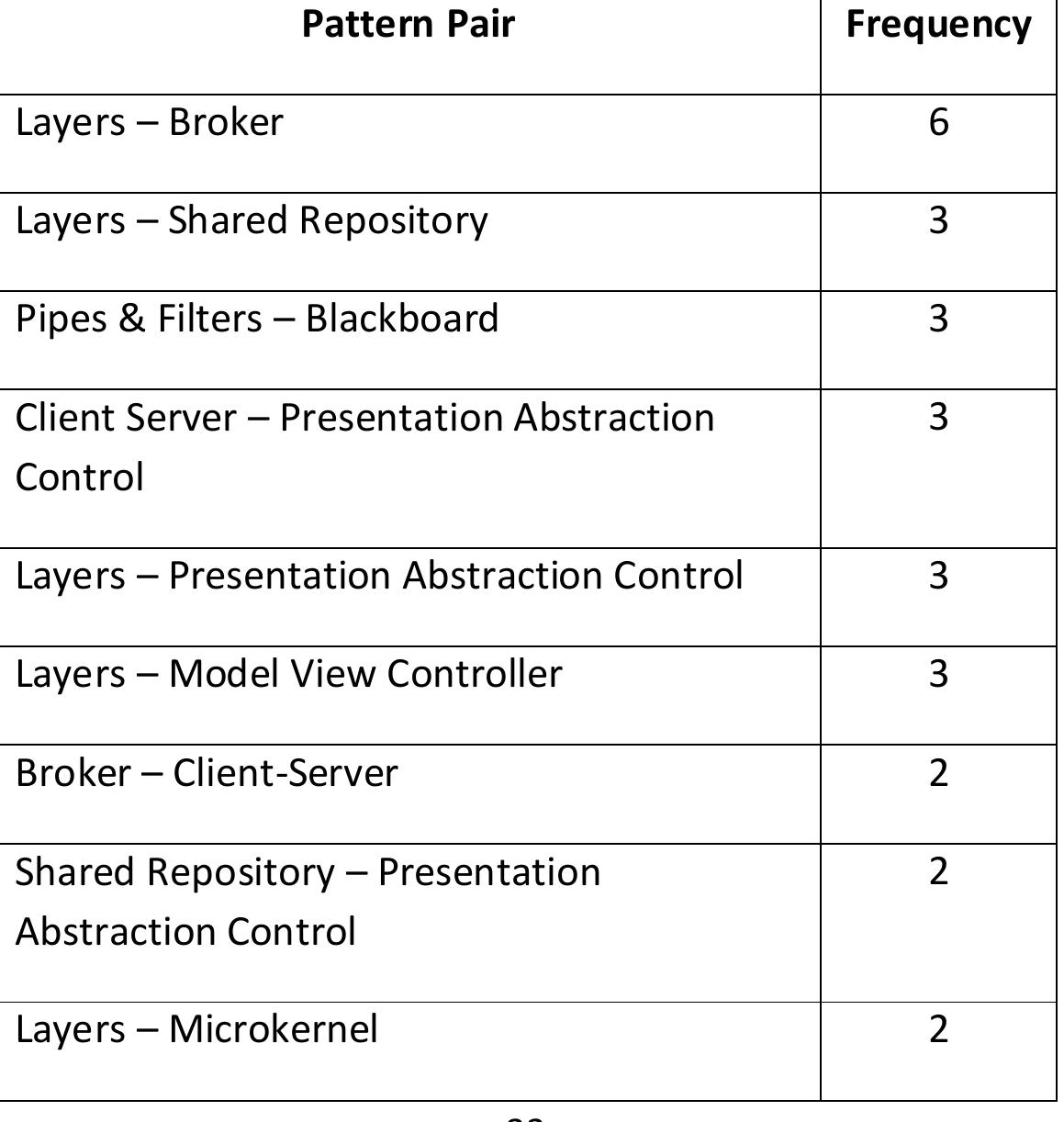
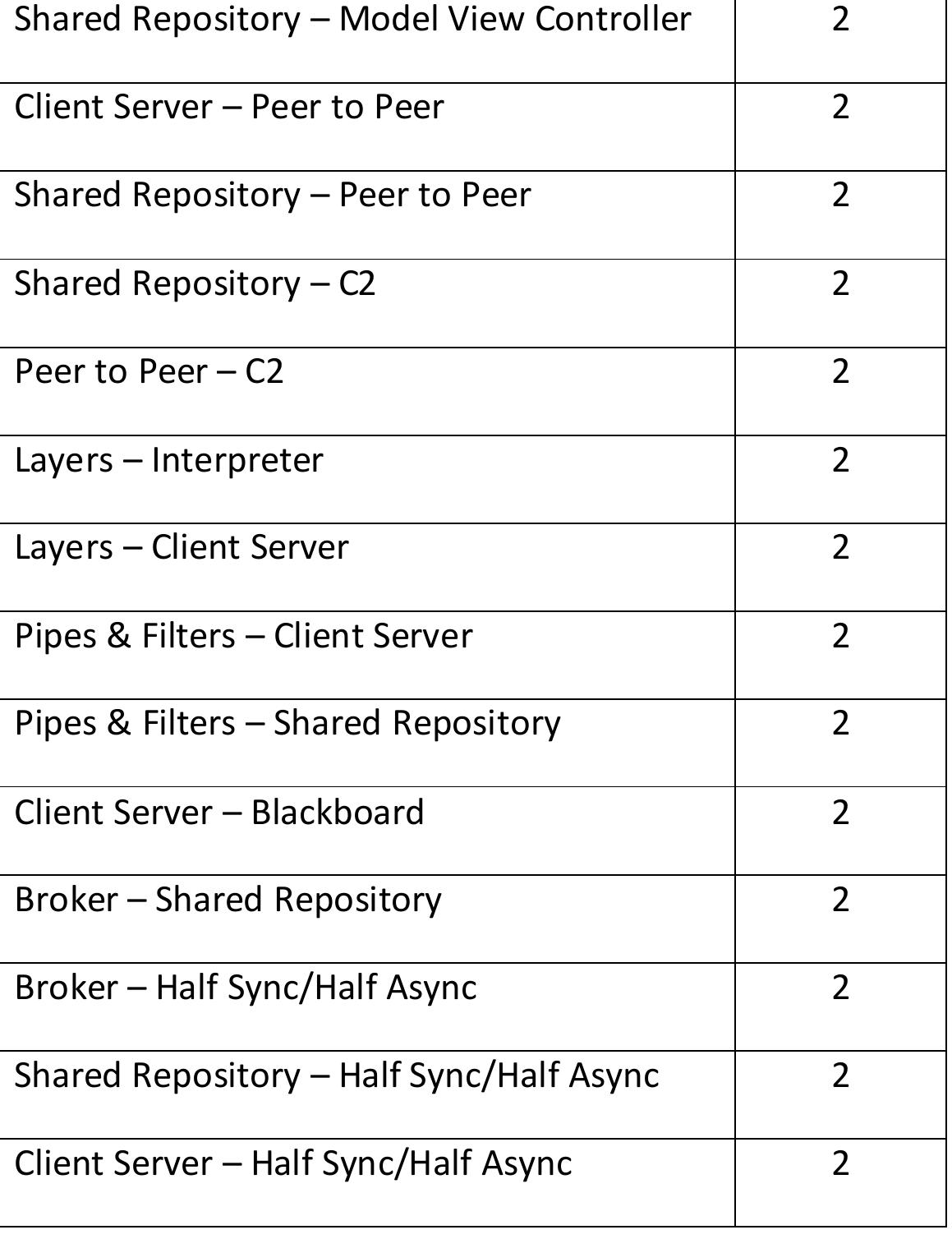
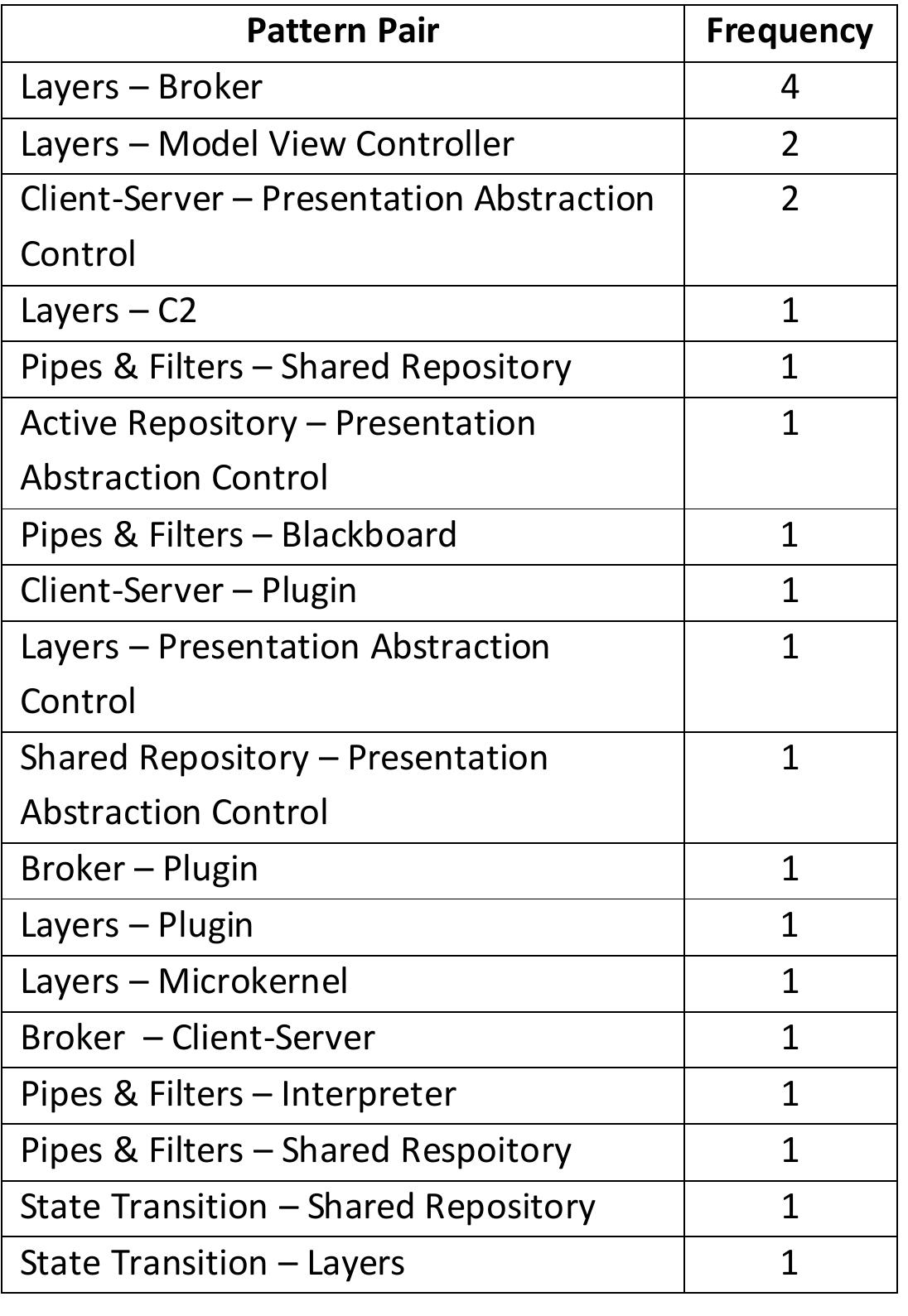
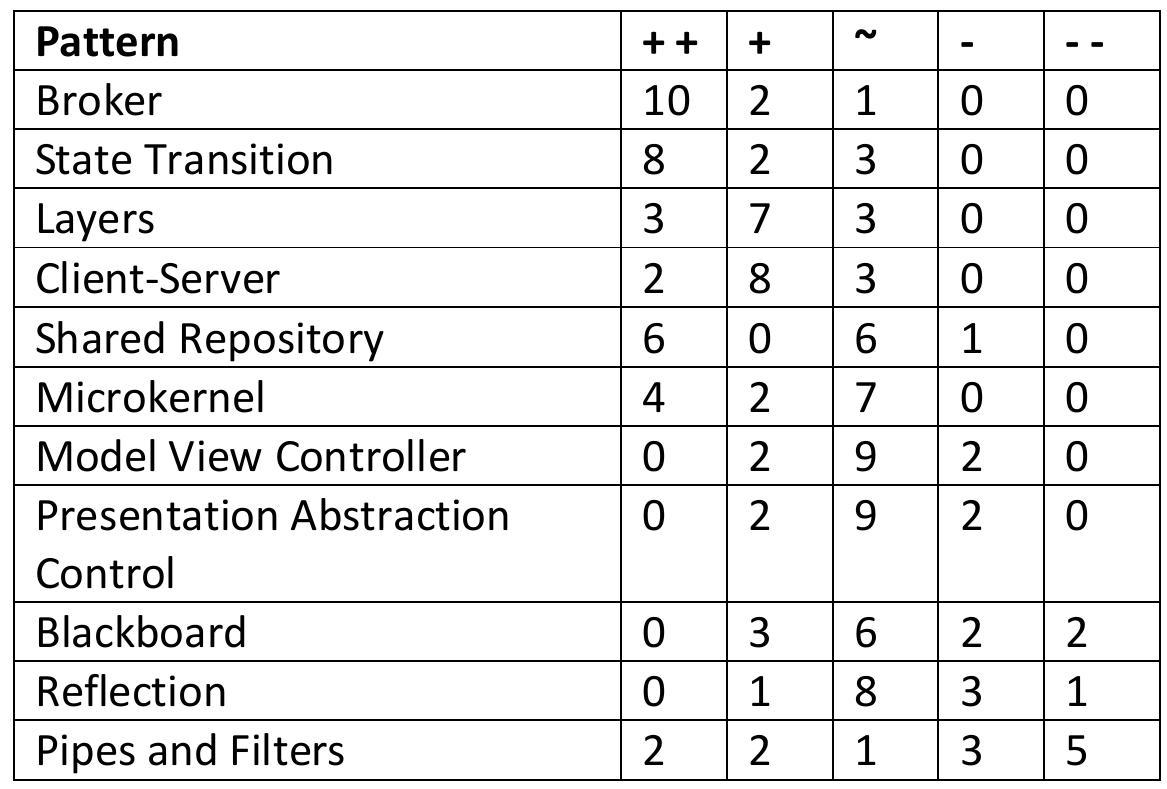
Architecture patterns are an important tool in architectural design. However, while many architecture patterns have been identified, there is little in-depth understanding of their actual use in software architectures. For instance, there... more
Architecture patterns are an important tool in architectural design. However, while many architecture patterns have been identified, there is little in-depth understanding of their actual use in software architectures. For instance, there... more
Cooperating objects (COs) is a recently coined termused to signify the convergence of classical embedded computersystems, wireless sensor networks and robotics and control. Wepresent essential elements of a reference architecture for... more
The landscape of warehouse operations is undergoing a transformative shift with the advent of cutting-edge material handling innovations. From autonomous mobile robots (AMRs) and advanced conveyor systems to AI-driven inventory management... more
The warehousing world has witnessed a significant transformation, with technological advancements reshaping the landscape. Material Handling Innovations are critical in optimizing operations, improving efficiency, and reducing costs. By... more
Ayman Abdalla as well for being my local supervisor. I thank him for his consistent support and encouraging comments during the research stages. I also thank Dr. Shakeel Ahmad for the useful discussion on the research and for his advice... more
Public Key Infrastructure (PKI) schemes were first proposed in 1978 and standardized in 1988, yet, unlike most cryptographic schemes, PKI schemes were never rigorously defined. Achieving provable security for PKI is necessary and long... more
A typical component-based system architecture comprises a set of components that have been purposefully designed and structured to ensure that they have "pluggable" interfaces and an acceptable match with a defined system context.... more
The migration of monolithic applications to the cloud is a popular trend, with microservice architecture being a commonly targeted architectural pattern. The motivation behind this migration is often rooted in the challenges associated... more
The intensive development of hardware and software tools provides many opportunities for solving various real-world tasks, such as working with large data sets. This, in turn, is a powerful incentive and opportunity for the development of... more
Serverless computing and Function-as-a-Service (FaaS) have become the new “new hotness” in cloud computing. Since FaaS completely abstracts away the infrastructure, developers are left with having to write only their app logic — a very... more
Architecture conformance checking is an important activity of architecture enforcement where the architect ensures that all architecture concepts are implemented correctly in the source code. In order to support the architect, a lot of... more
Electronic voting requires voting privacy to protect the voter anonymity. We present a novel design framework for credential management called Voting Credential Management System (VCMS) which preserves voting privacy against advanced... more
Background Healthcare relies on health information systems (HISs) to support the care and receive reimbursement for the care provided. Healthcare providers experience many problems with their HISs due to improper architecture design. To... more
Legislative analysis: Methodology for the analysis of groups and coalitions. In EPRINTS-BOOK-TITLE s.n..
In this paper, we introduce Attribute-Based Signatures with User-Controlled Linkability (ABS-UCL). Attribute-based signatures allow a signer who has enough credentials/attributes to anonymously sign a message w.r.t. some public policy... more
This paper describes our research on both the detection and subsequent resolution of recognition errors in spoken dialogue systems. The paper consists of two major components. The first half concerns the design of the error detection... more
The GALAXY-II architecture, comprised of a centralized hub mediating the interaction among a suite of human language technology servers, provides both a useful tool for implementing systems and also a streamlined way of configuring the... more
In this talk, we advocate the view that simplification of nomenclature, stated in linguistically well-motivated concepts, leads to an ideal IL for human language communication systems including multilingual machine translation and spoken... more
To support the development of adaptive, dynamic hypertext systems at CoGenTex, we have been evolving Exemplars, a rule-based object-oriented framework for dynamic hypertext generation. In this paper, we sketch our approach to designing... more
To our knowledge, no current software development methodology explicitly describes how to transit from the analysis model to the software architecture of the application. This paper presents a method to derive the software architecture of... more
This paper proposes a new efficient signature scheme from bilinear maps that is secure in the standard model (i.e., without the random oracle model). Our signature scheme is more effective in many applications (e.g., blind signatures,... more
The paper discusses the development of a multi-agent manufacturing control system for an industrial application. This multi-agent system follows the PROSA reference architecture and applies an ant colony design (stigmergy) to provide... more
This paper presents the design of a holonic manufacturing execution system. The design is an instantiation of the PROSA reference architecture [1] augmented with coordination and control mechanisms inspired by natural systems i.e. food... more
Engineering environments for flexible and easy to maintain multi-agent manufacturing control systems
Current manufacturing control systems are not easy to maintain. They are vulnerable towards changes in the production mix or towards performance goal changes. These systems are also known for their integration and interoperability... more
This manuscript presents a design for the emergent generation of short-term forecasts in coordination and control systems. Food foraging behavior in ant colonies constitutes the main inspiration for this design. The research team applies... more
Depending on the physical structuring of large distributed safety-critical real-time systems, one can distinguish federated and integrated system architectures. The DE-COS architecture combines the complexity management advantages of... more
The architecture of a software system is both a success and a failure factor. Taking the wrong architectural decisions may break a project, since such errors are often systematic and affect cross-cutting aspects of the system to be built.... more
Manufacturing systems can be very complex and are often costly to develop and operate. Simulation technology has been shown to be an effective tool for optimizing manufacturing system design, operations, and maintenance procedures.... more
Manufacturing systems can be very complex and are often costly to develop and operate. Simulation technology has been shown to be an effective tool for optimizing manufacturing system design, operations, and maintenance procedures.... more
Manufacturing systems can be very complex and are often costly to develop and operate. Simulation technology has been shown to be an effective tool for optimizing manufacturing system design, operations, and maintenance procedures.... more
Recently, Semantic Web Services have been increasingly adopted to search, access and manipulate information made available from autonomous and heterogeneous systems interacting in a P2P environment. Platform independency is obtained and... more
Numerous projects in the area of Real-World Internet (RWI), Internet of Things (IoT), and Internet Connected Objects have proposed architectures for the systems they develop. All of these systems are faced with very similar problems in... more
In this paper we propose a meta-model for architectures with heterogeneous multimedia components. Currently, a generic solution does not exist to automatically deploy a distributed architecture based on multimedia components. The... more
Software Architecture has been recognized both by Academia and software industries as the most promising approach to tackle the problems in the era of Finance, Communications, Medical, Run-time applications etc. Software architecture... more
The paper's focus point on understanding of software system with its development on the concept of software architecture styles in the field of medical domain. In order to fasten the software maturity process for patients' recovery and... more




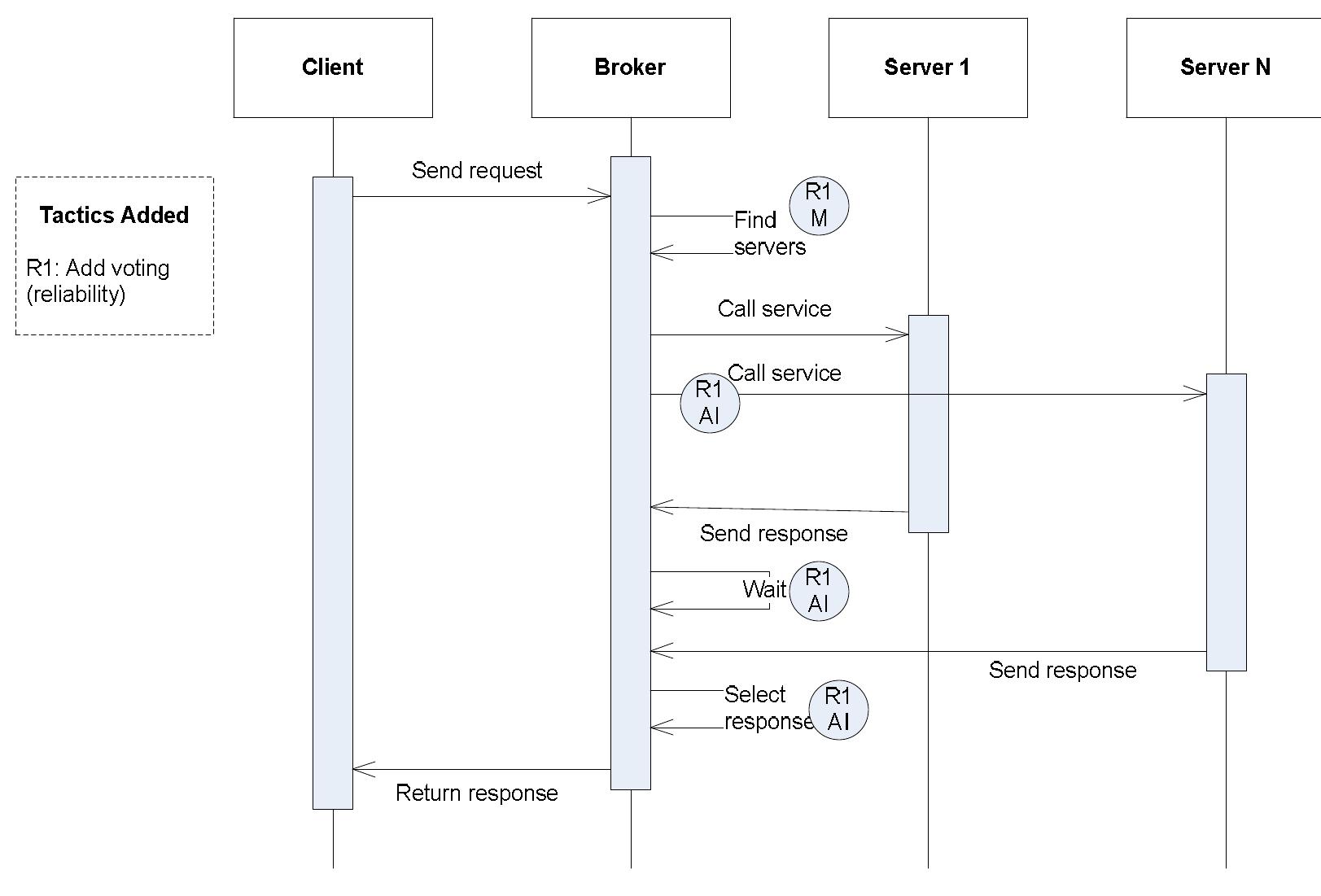
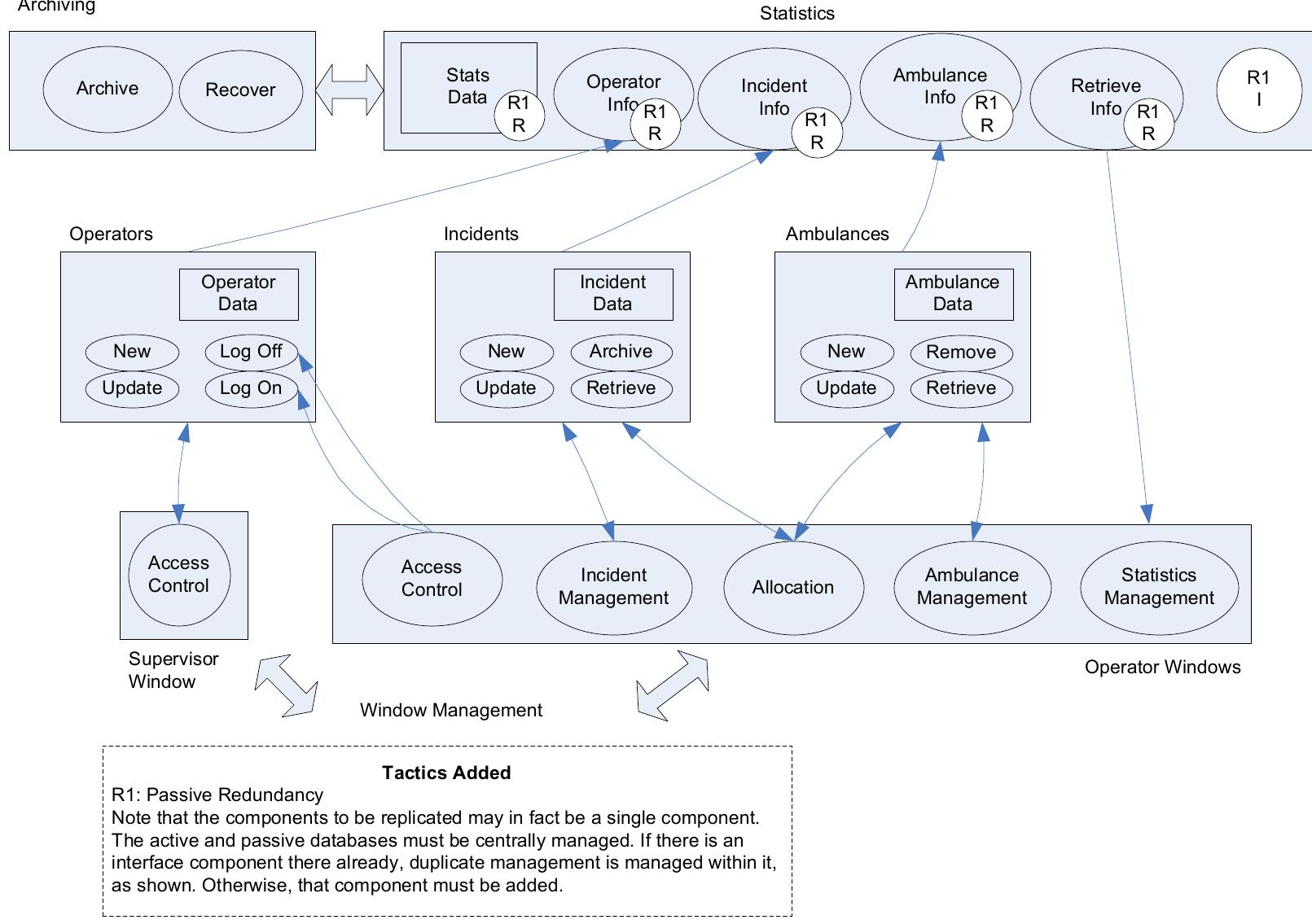
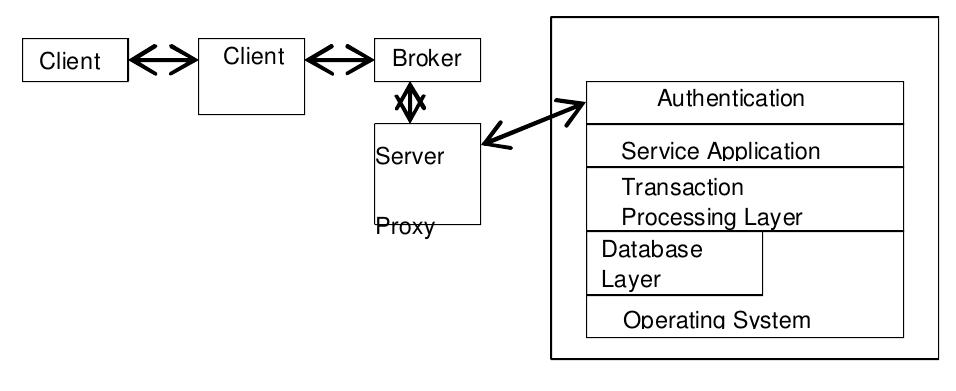
![Ambulance: The following diagram is from an ambulance information system, from [125]. The upper rectangle labeled “Statistics” is a Shared Repository. We wish to improve reliability by duplicating the repository, using the Passive Redundancy (Warm Spare) pattern. (Note: this improves the availability of the system by allowing the system to continue to operate if one of the databases is to fail; reliability of data integrity is clearly already supported through the archive and recover components.) This diagram is problematic because it isn’t clear what the large rectangles mean. Most appear to designate association, such as the lower rectangle labeled “Operator Windows,” but the one we are concerned with, the Statistics rectangle, may in fact designate containment within a common database component. Furthermore, we were unable to obtain the book that contains this diagram, so further information is The following diagram is from an ambulance information system, from [125]. The](https://figures.academia-assets.com/120841515/figure_009.jpg)
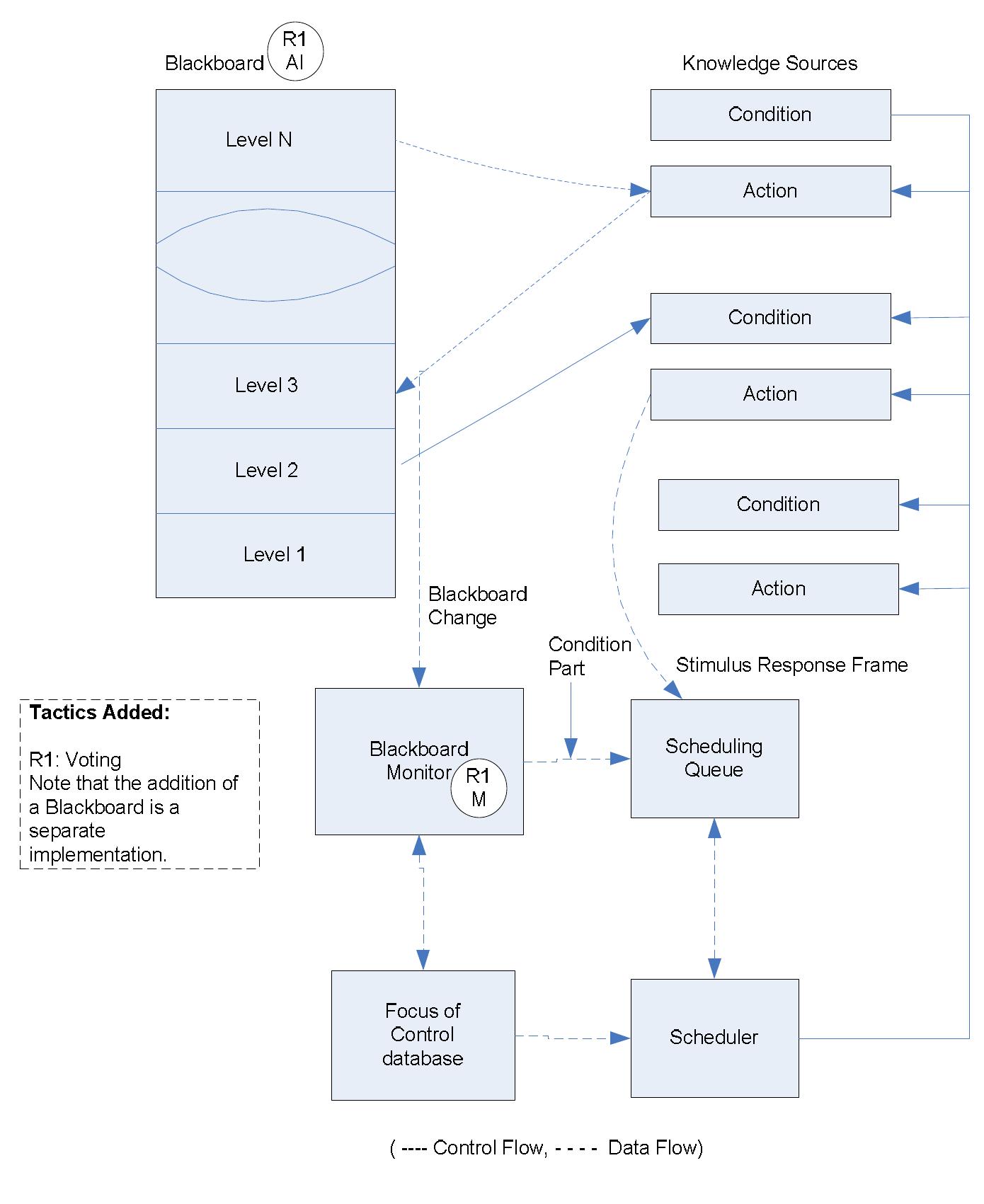
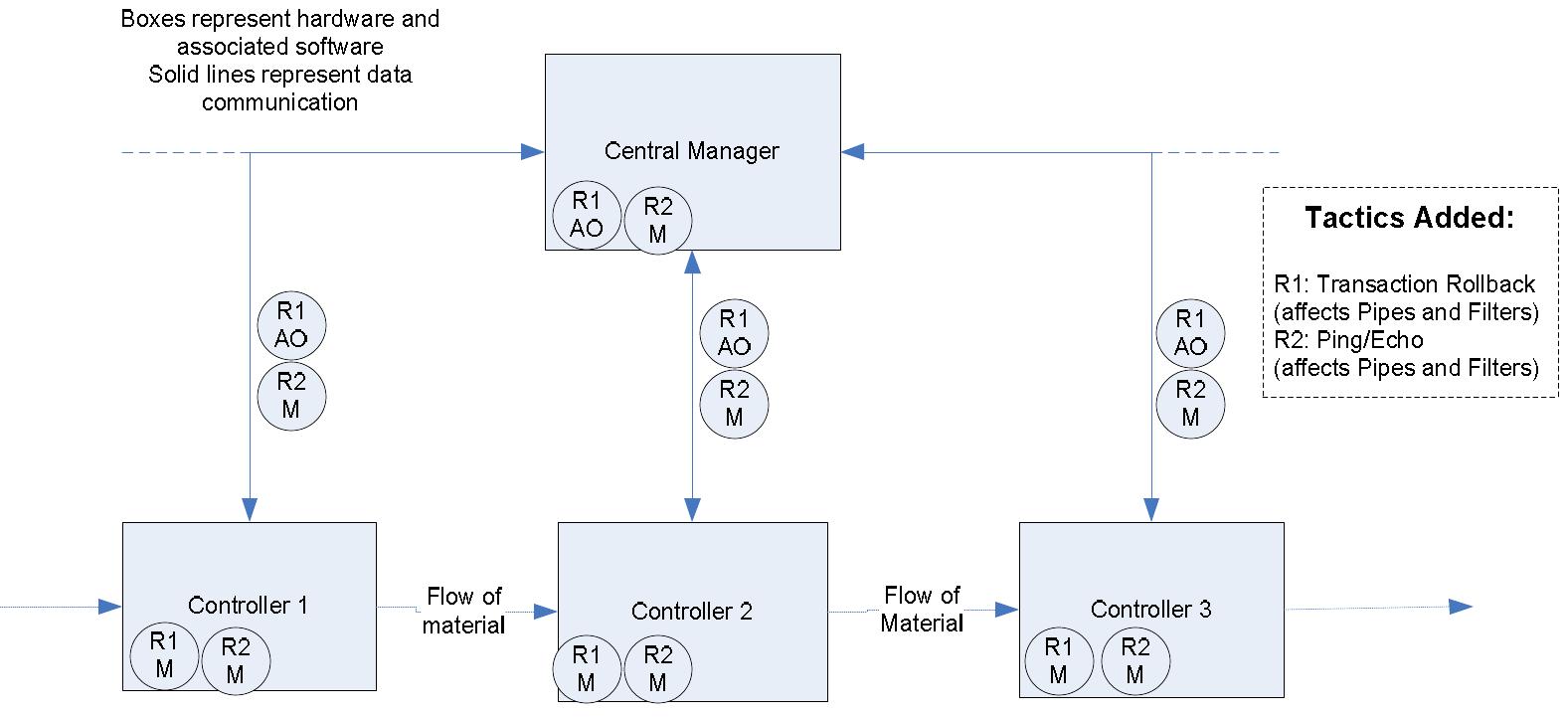

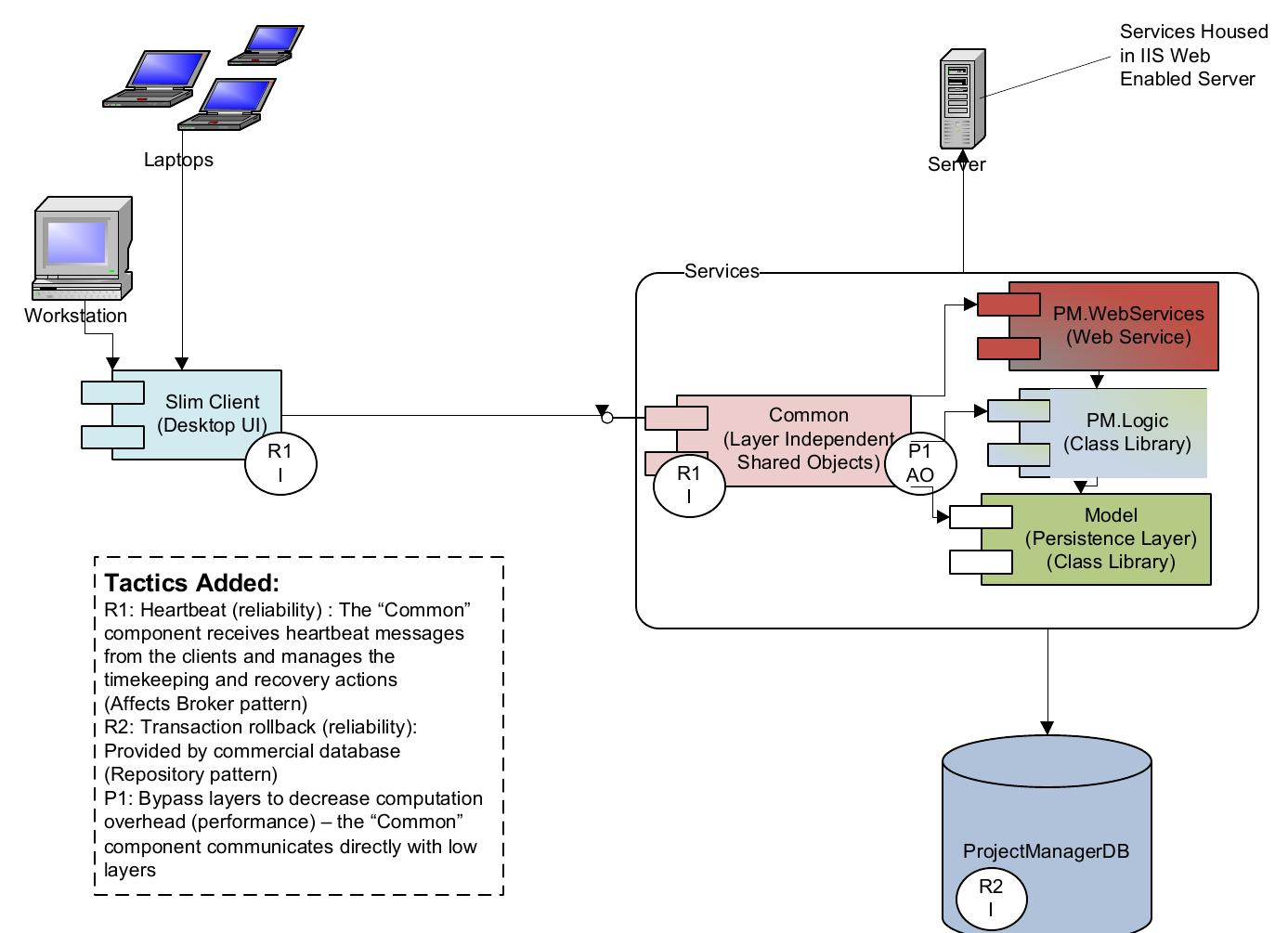

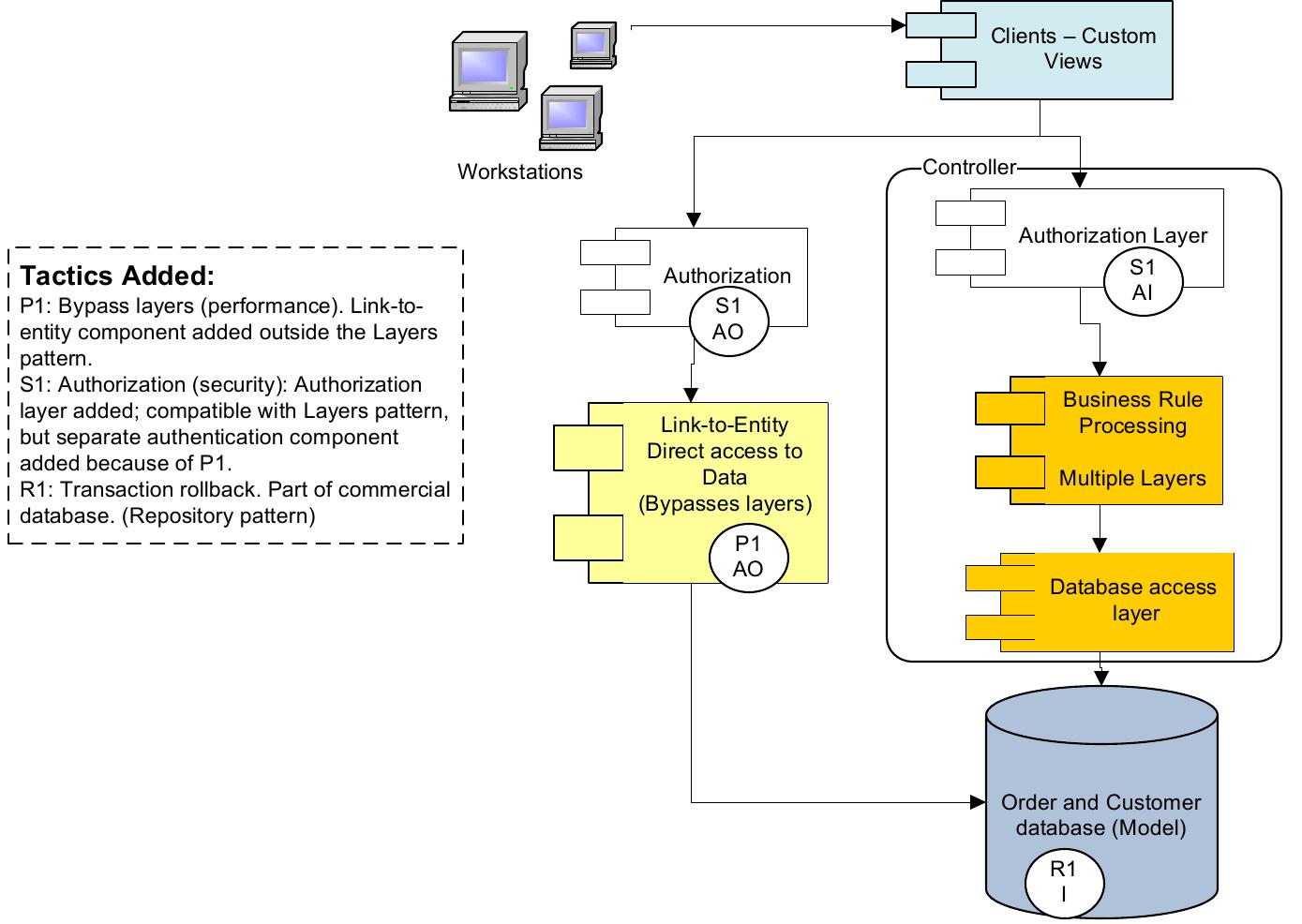


![activities and data flows, and are described at the bottom of the figure. Figure 6.2: Architecture design activities from [72], with pattern and tactic activities](https://figures.academia-assets.com/120841515/figure_020.jpg)


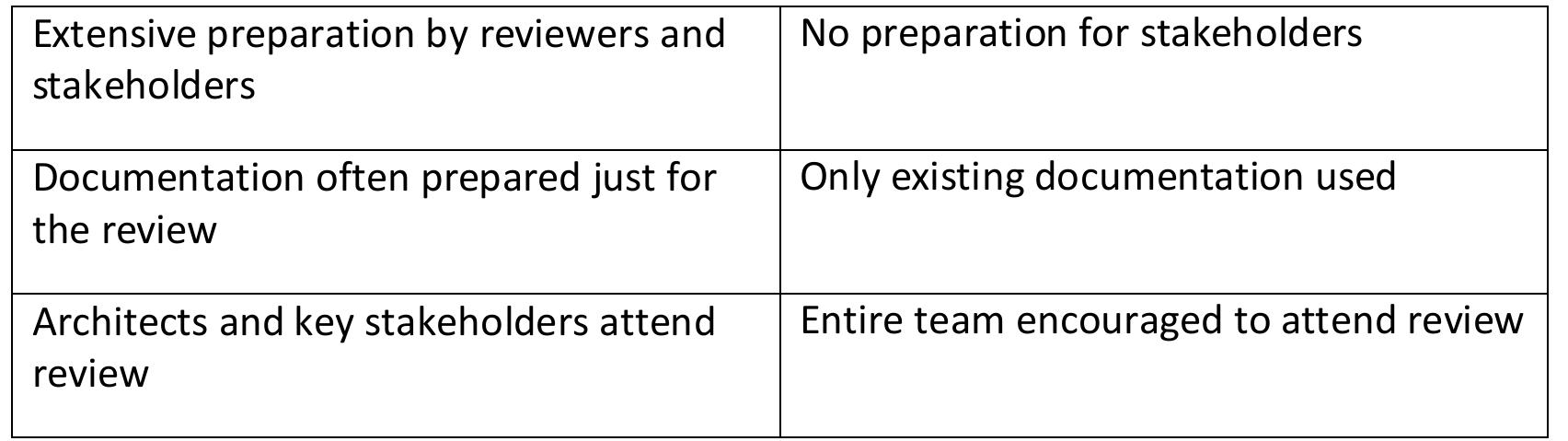
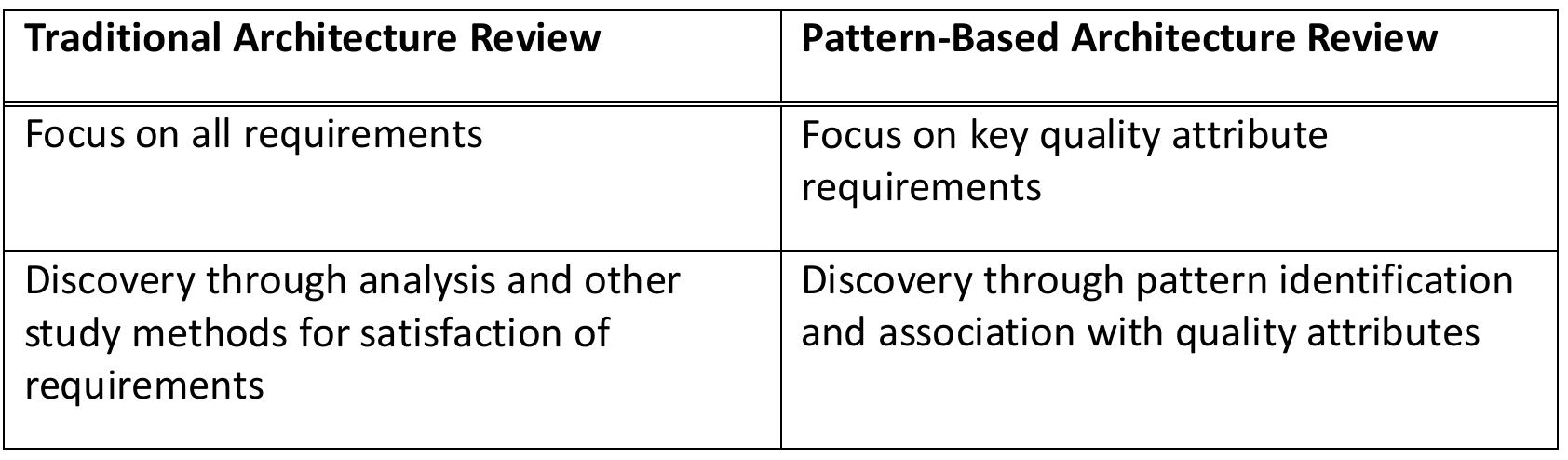
![The structure of Pattern-Based Architecture Reviews (PBAR) is based on architecture review processes, namely the AT&T review process [97], which one of the authors used while an employee there, as well as ATAM [15]. It is simpler than these processes chiefly in that the up-front work is reduced, and that the focus is narrowed to the quality attributes and patterns used. While architecture patterns may be identified during ATAM and other reviews, PBAR’s pattern focus also comes from reviews of organizations, where patterns were used to identify organizational issues [43]. The key differences between PBAR and traditional architecture reviews are summarized in this table: can be reduced through focusing review on the most important quality attributes, processes chiefly in that the up-front work is reduced, and that the focus is narrowed](https://figures.academia-assets.com/120841515/figure_024.jpg)




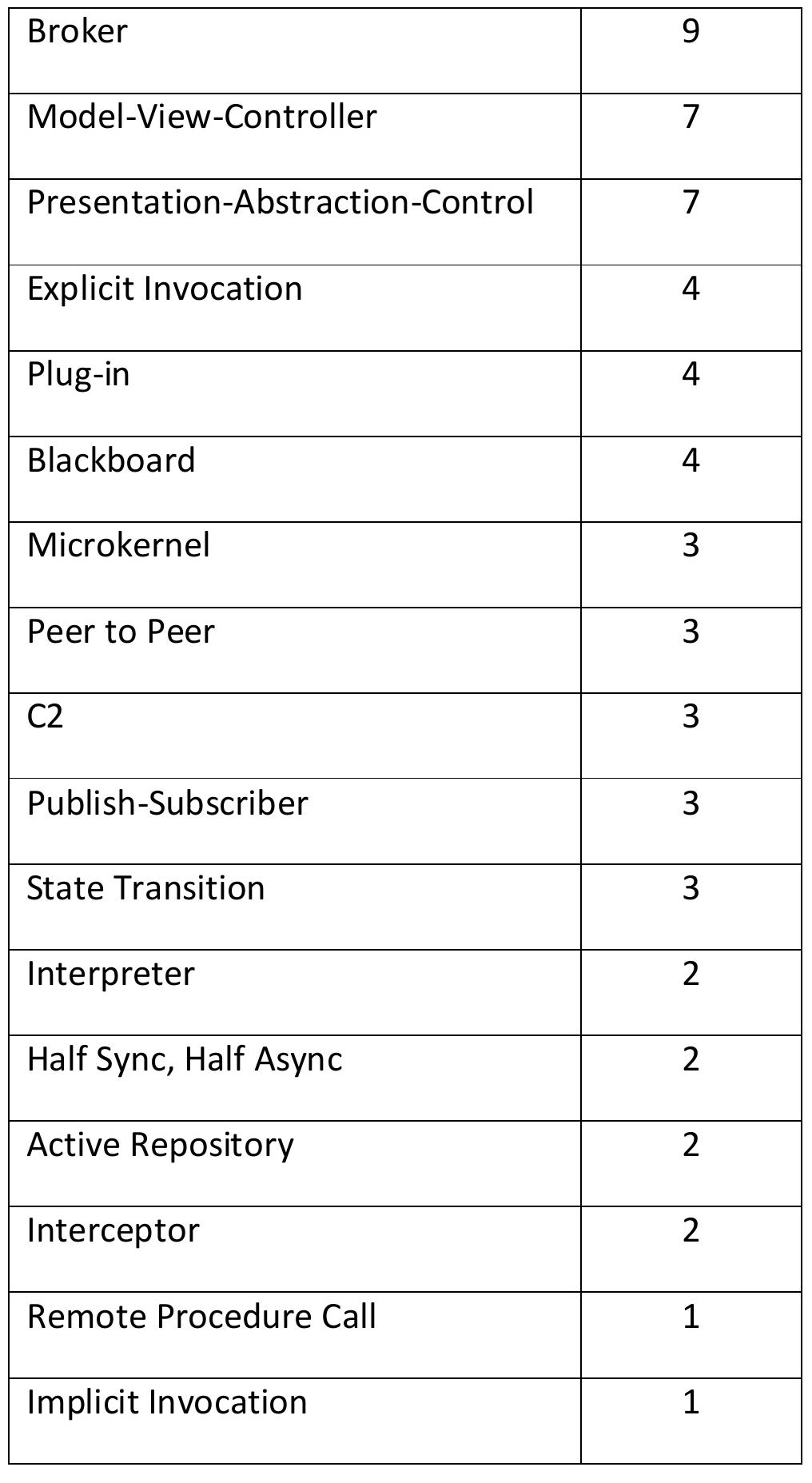
![Table 2.3: Pattern Frequency for the patterns State Transition [121] and Half Sync, Half Async [112].](https://figures.academia-assets.com/120841515/table_005.jpg)



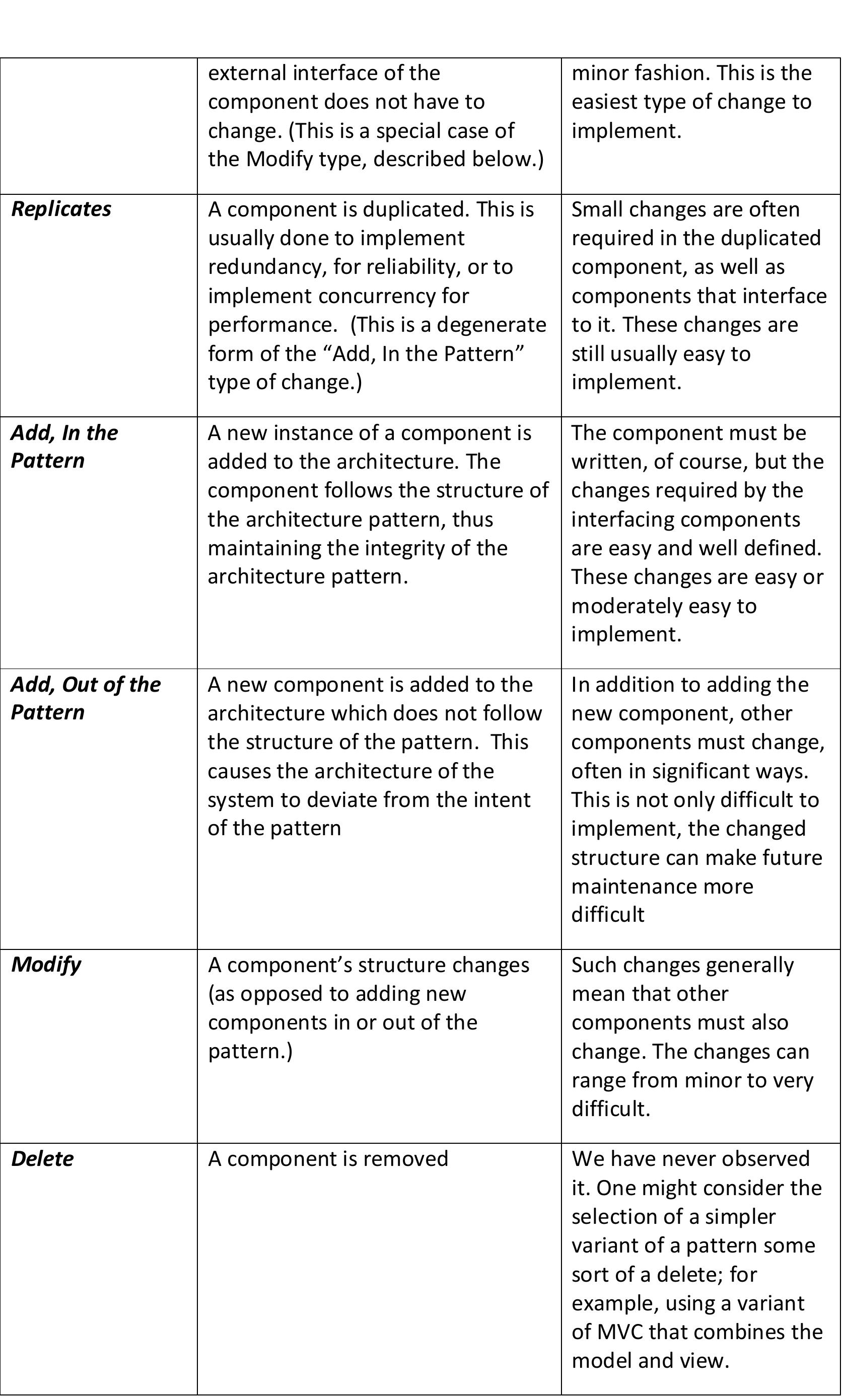
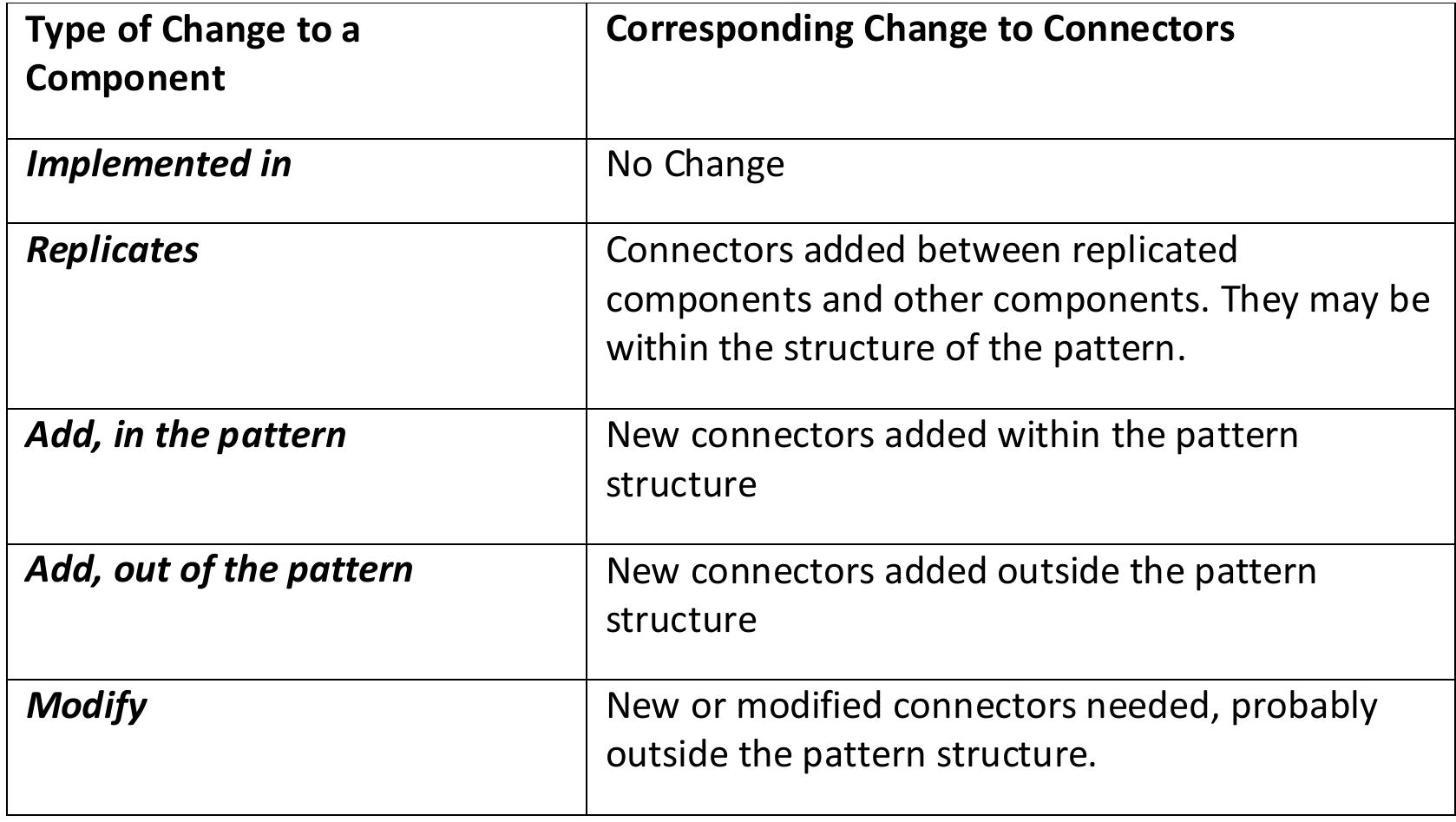
![offer examples in their book [33]), architectural decision documentation [129], and](https://figures.academia-assets.com/120841515/table_017.jpg)


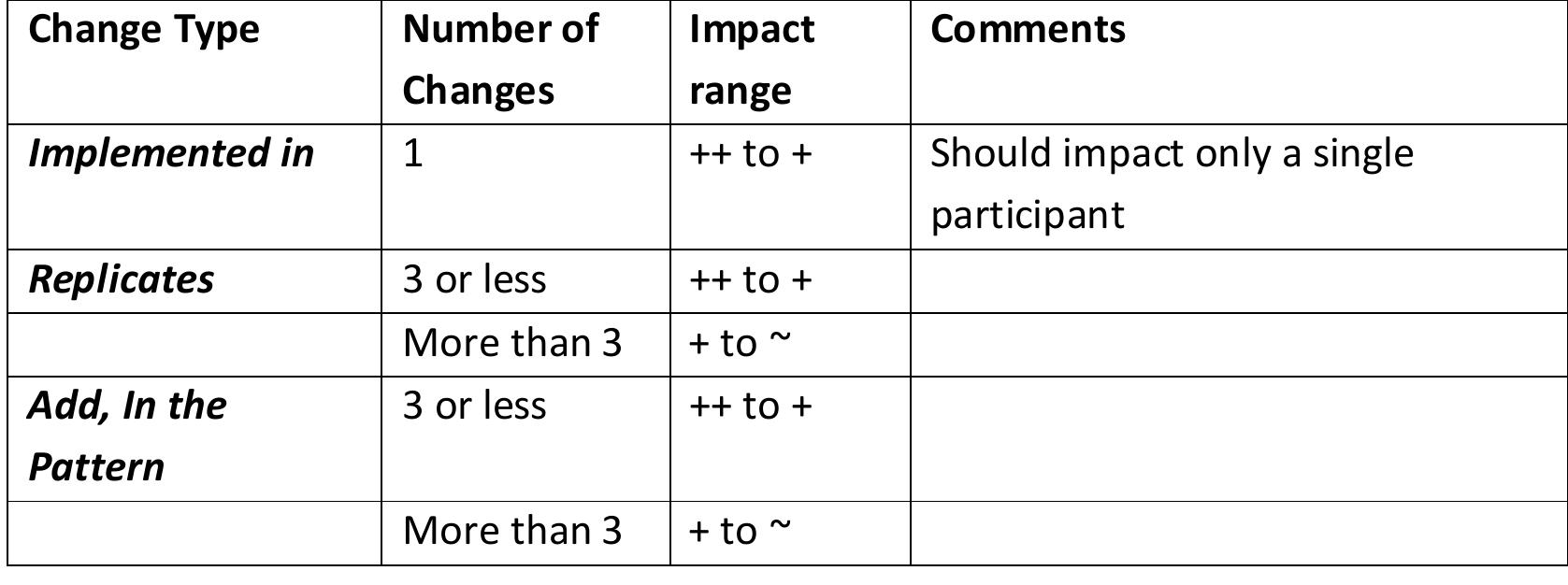
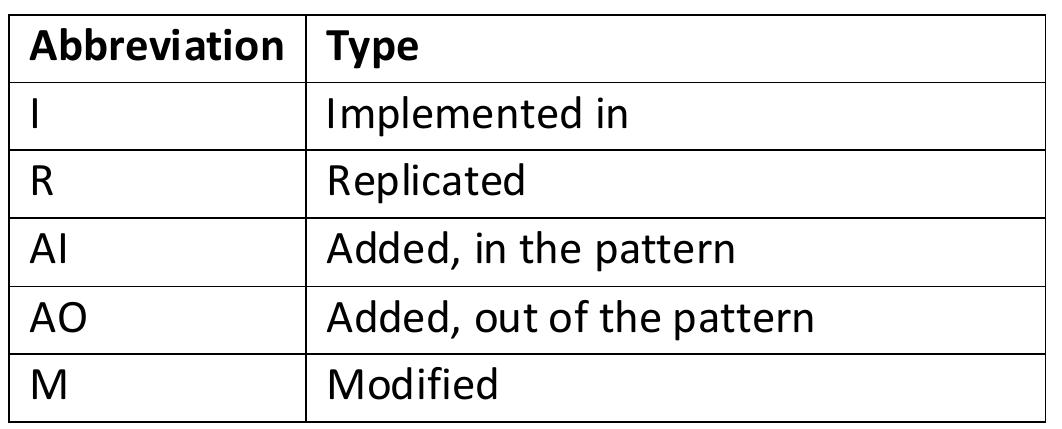
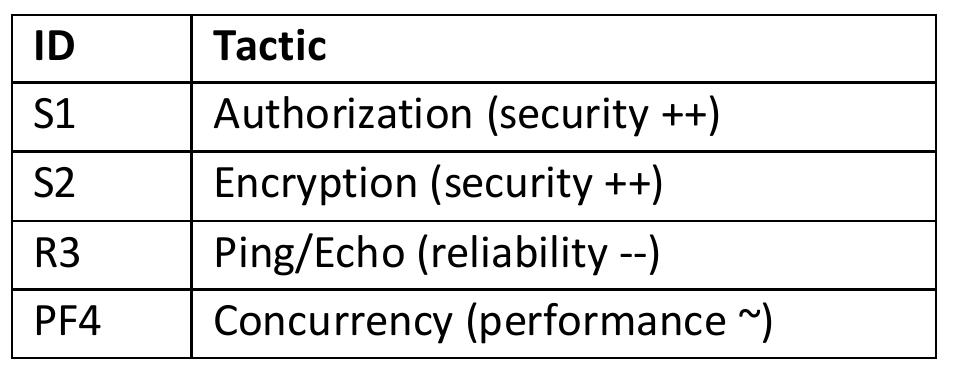
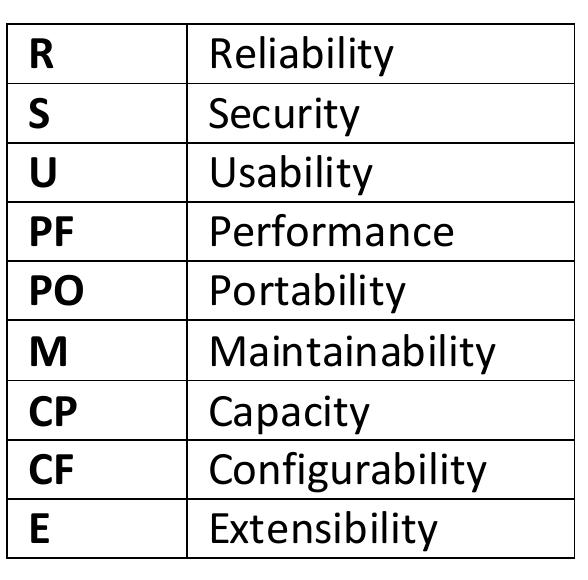
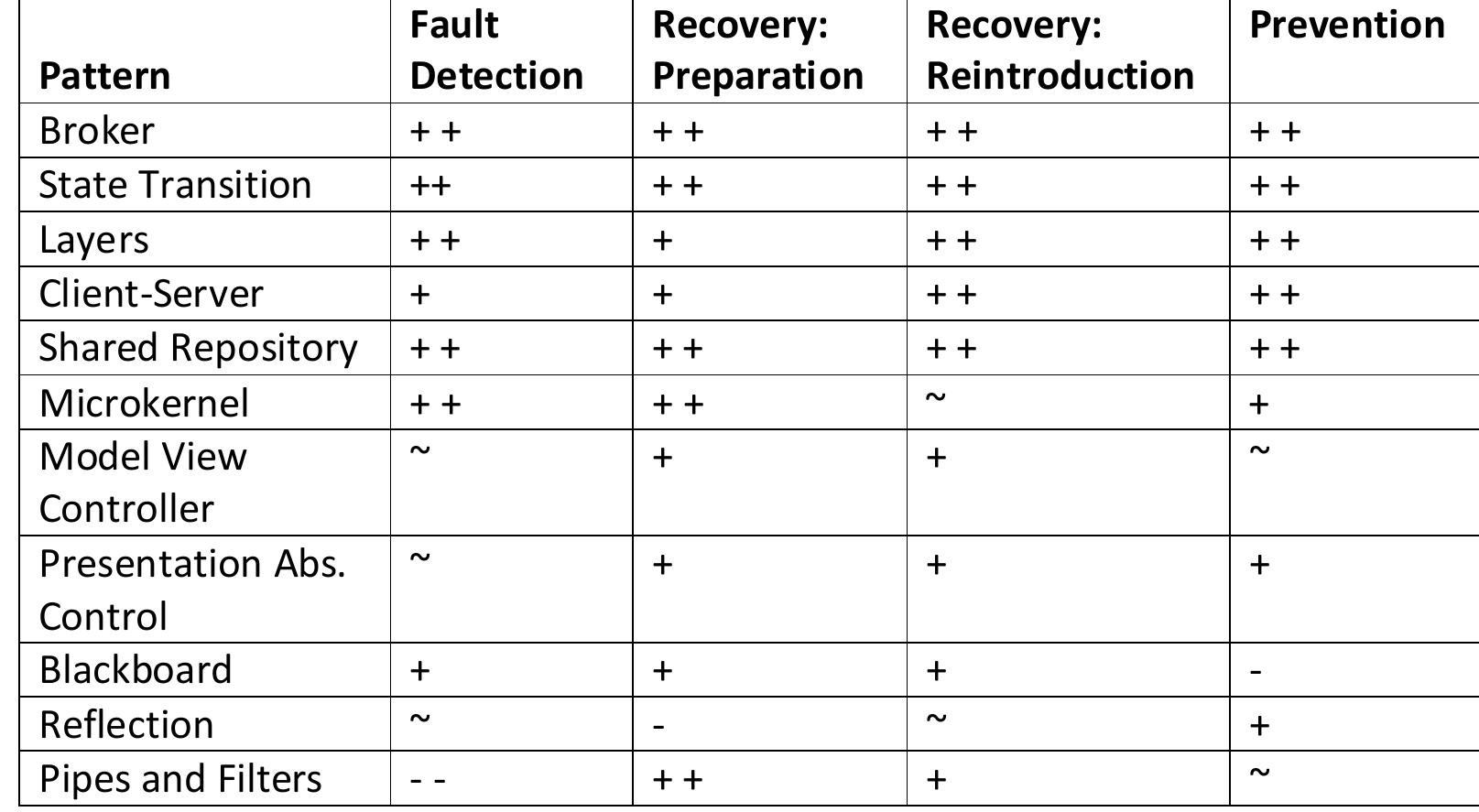
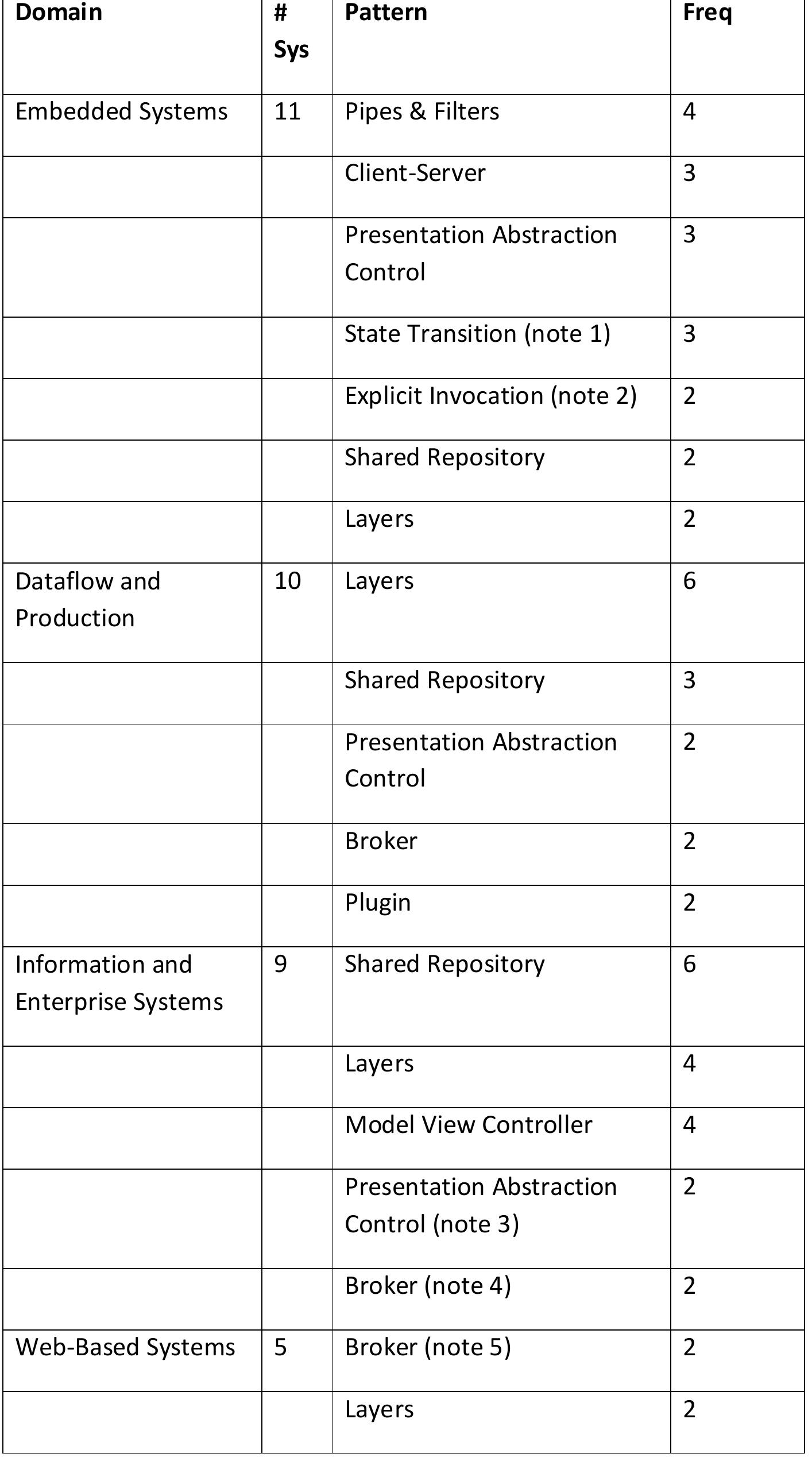
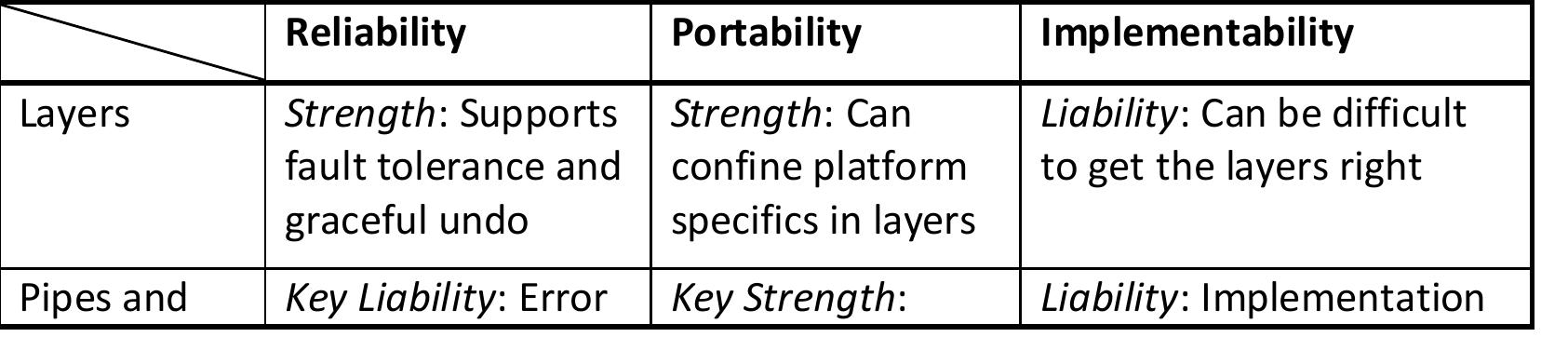
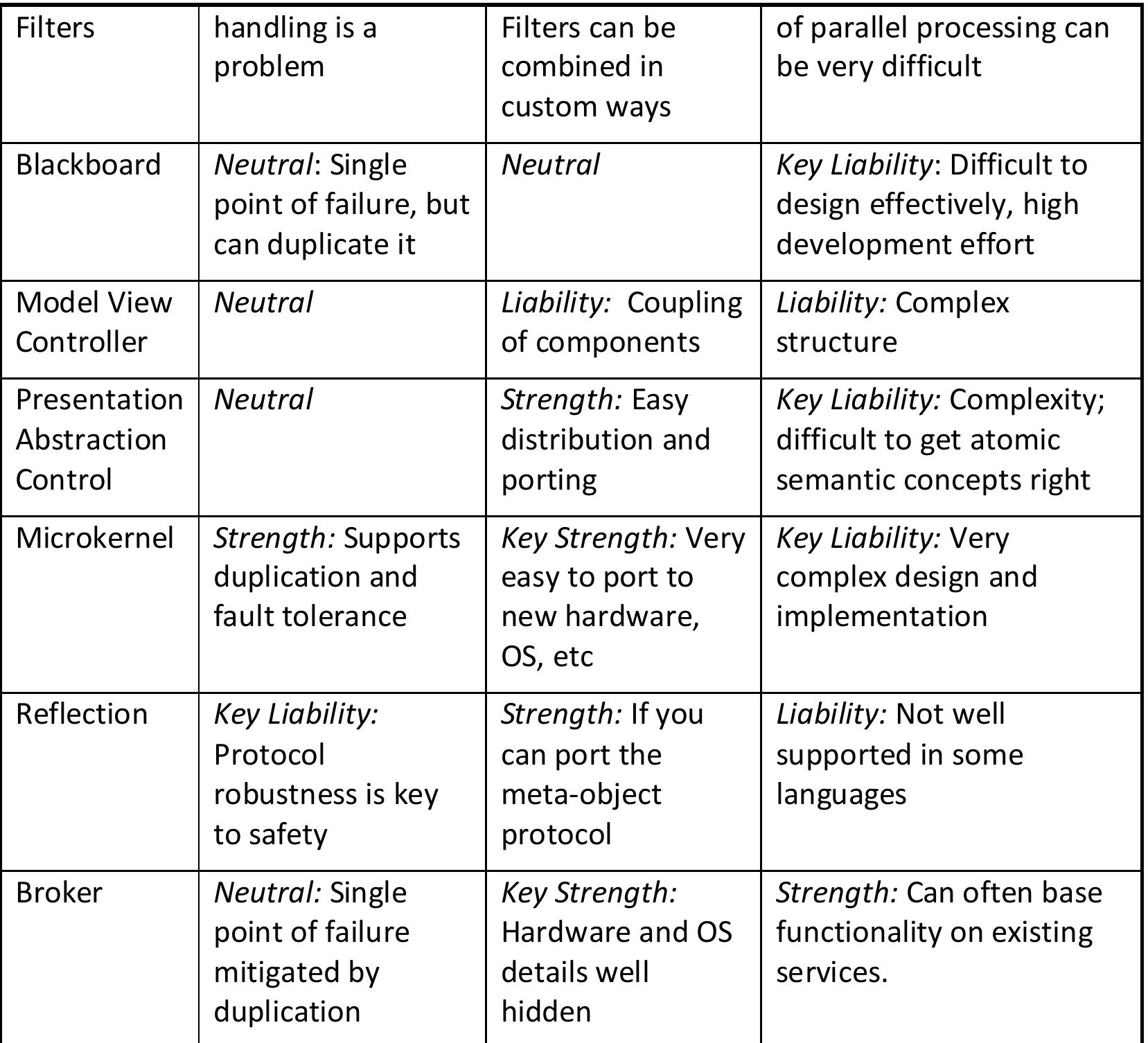
![Table 4.7: Common Architecture Patterns (From [11]) The following are short descriptions of some patterns and tactics used in this chapter:](https://figures.academia-assets.com/120841515/table_026.jpg)
![Table 5.5. Fault Tolerance Tactic Categories Full descriptions of these tactics can be found in [15]. We worked with these tactics because they are well known, and are described and organized conveniently. There](https://figures.academia-assets.com/120841515/table_030.jpg)
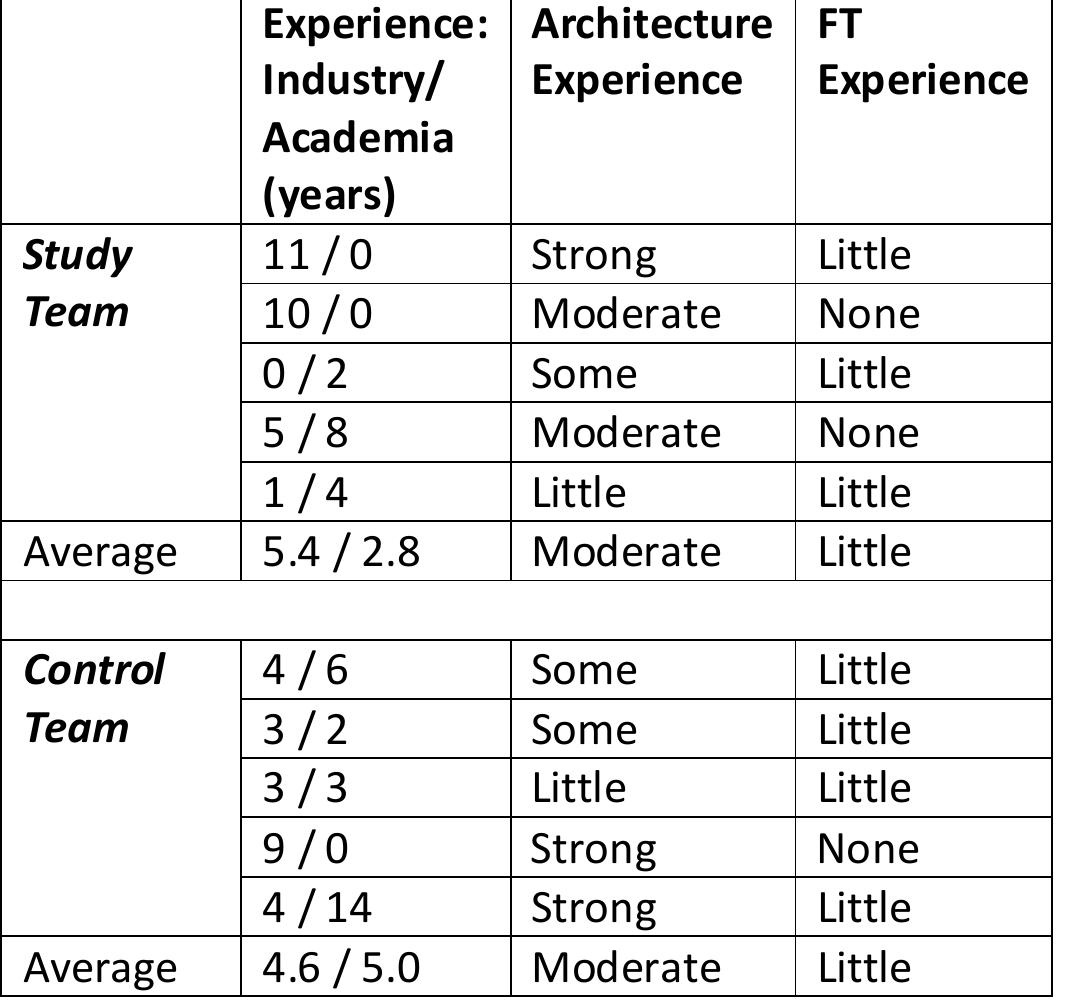
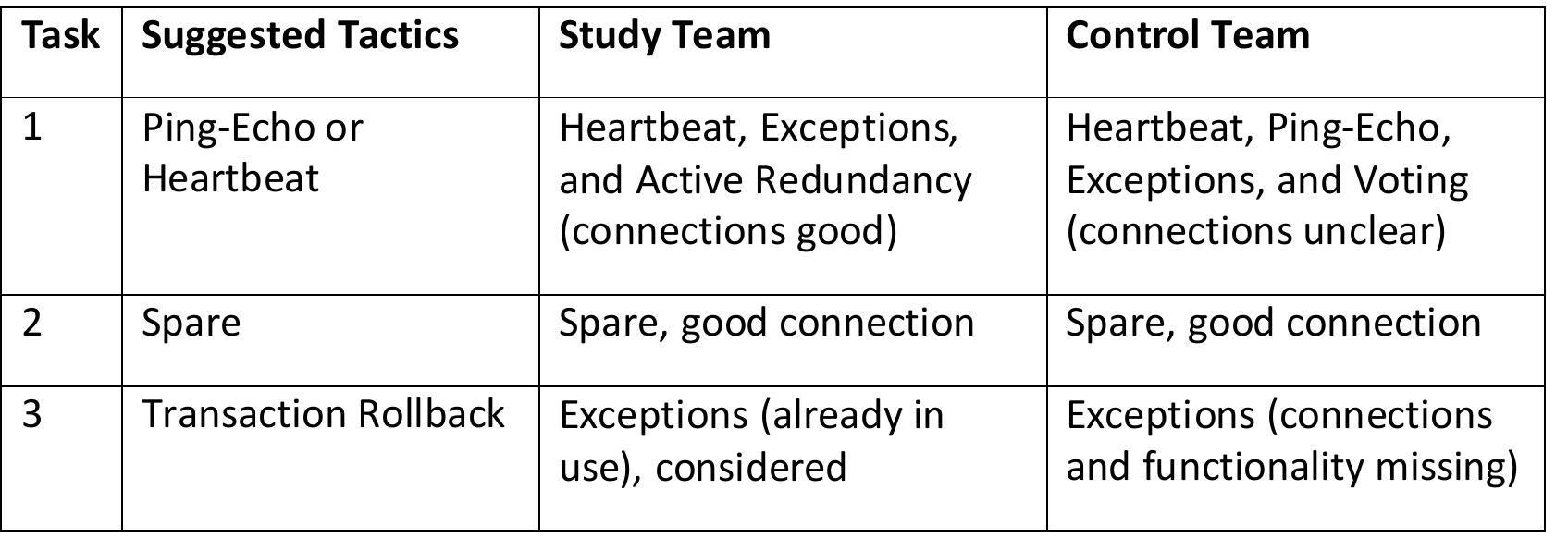


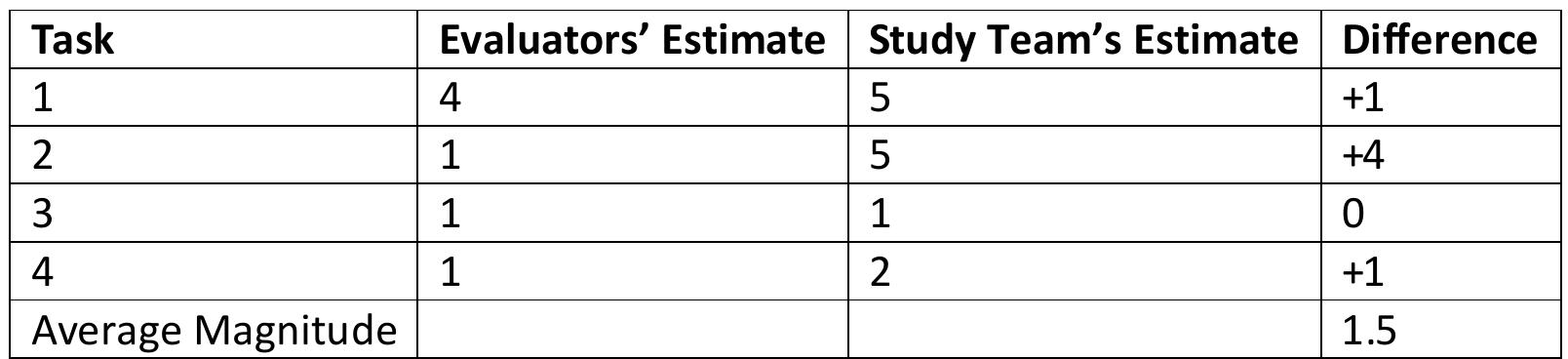

![Table 6.2: Categories of Impact of Common Reliability Tactics have not studied other reliability tactics (from Utas [130], Hanmer [60], or other sources) enough to know whether these trends are consistent; this is noted as future](https://figures.academia-assets.com/120841515/table_038.jpg)


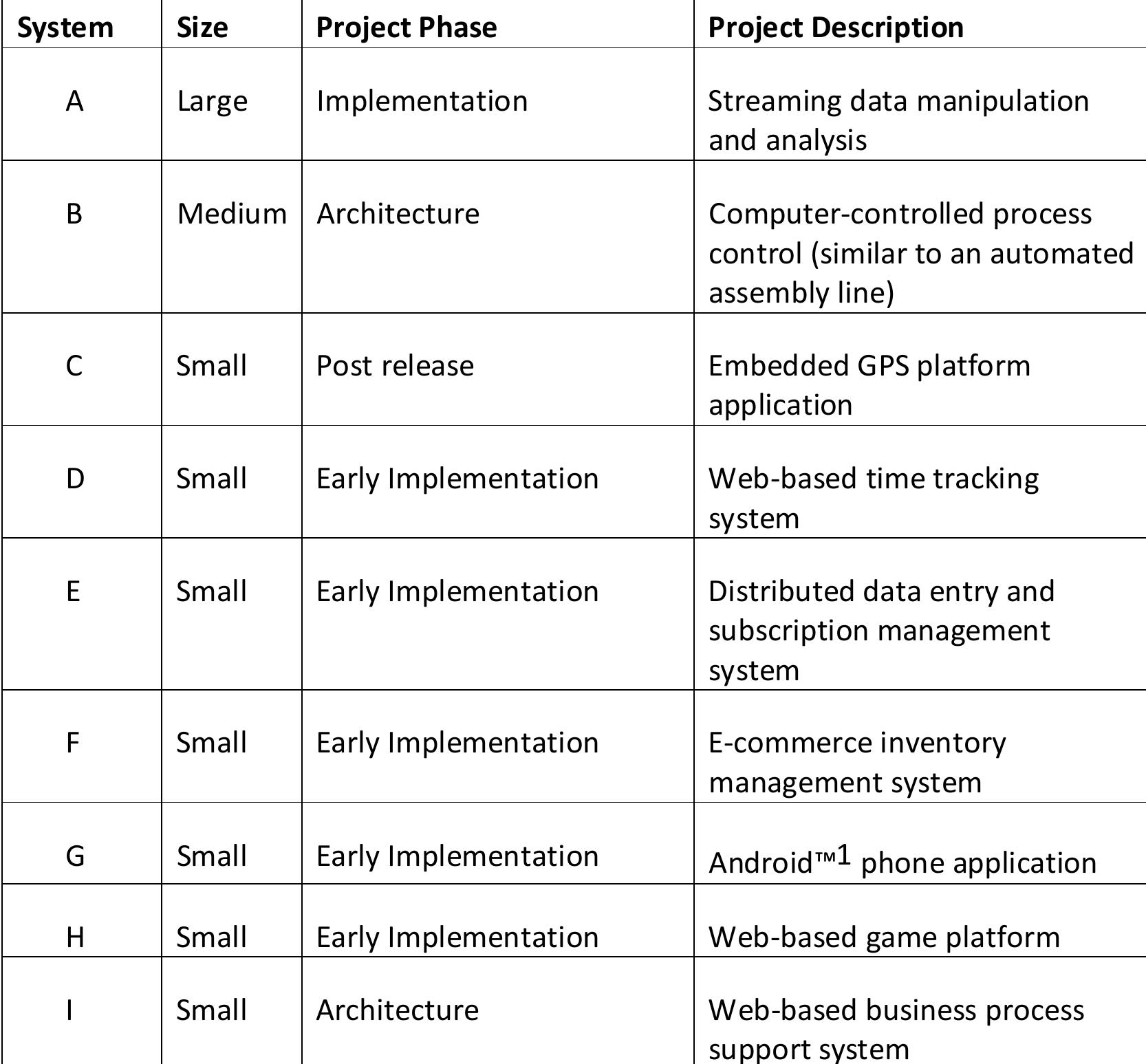

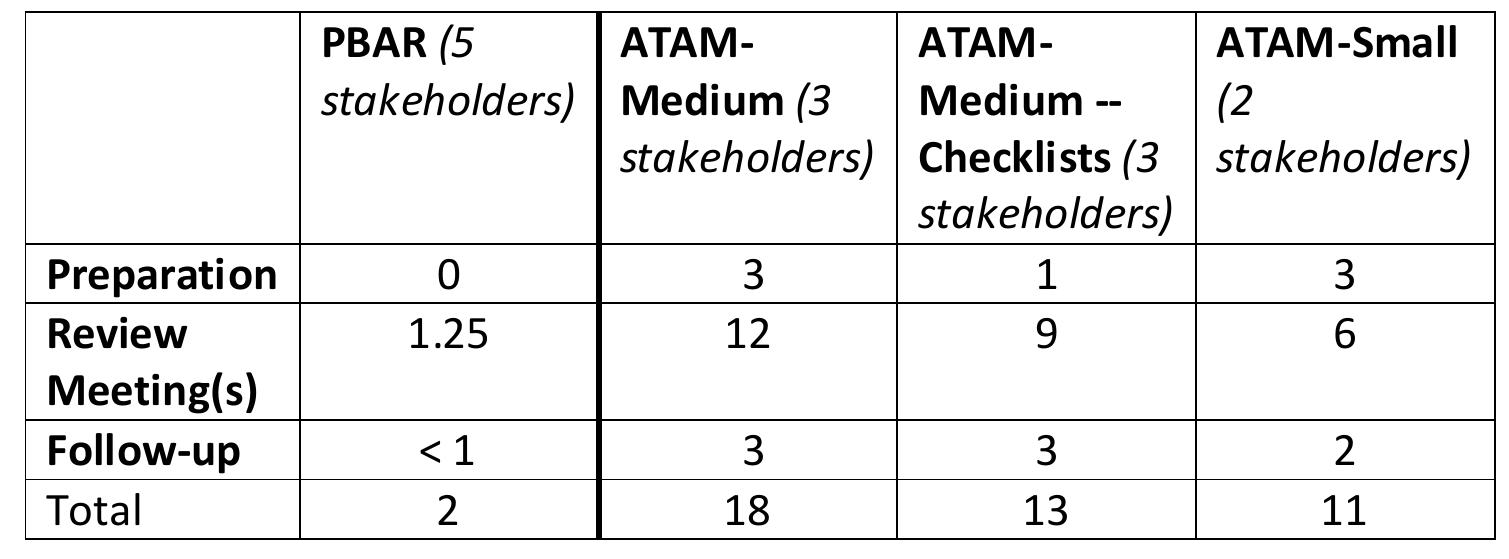
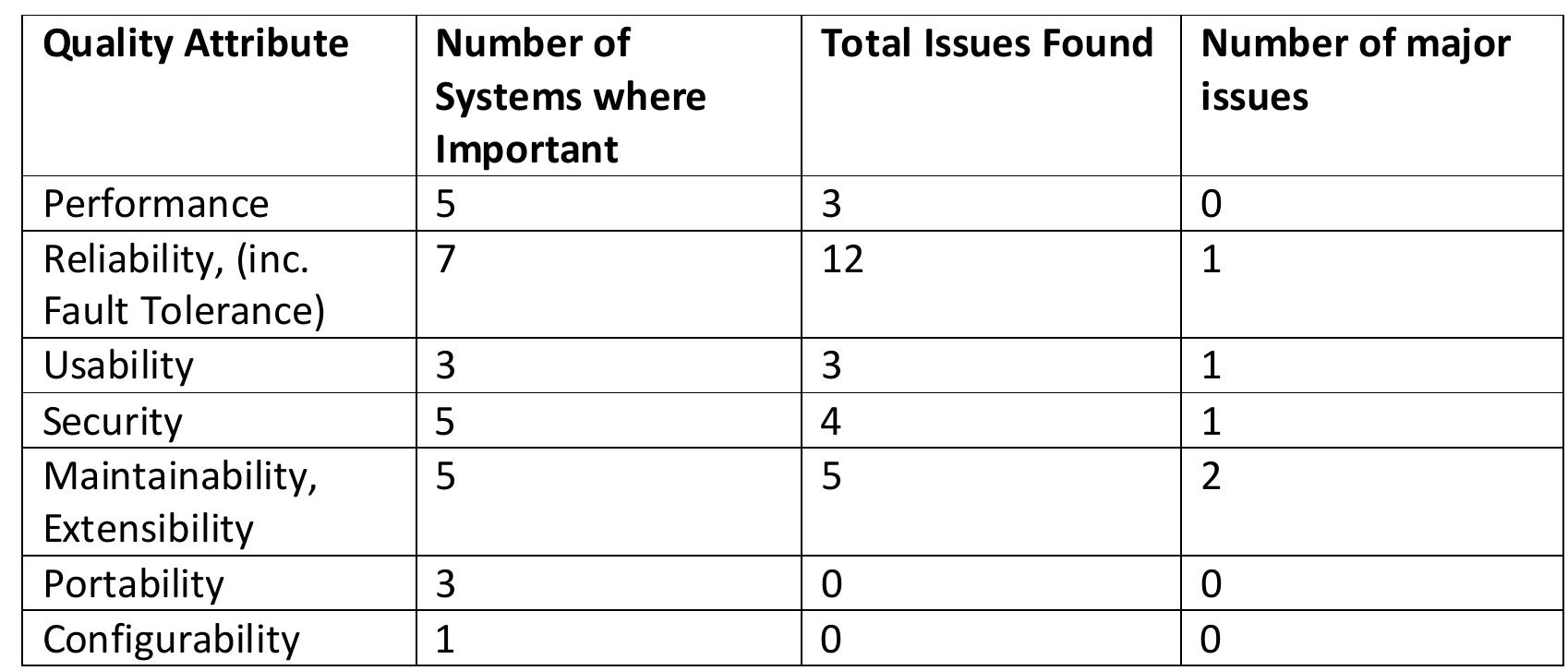
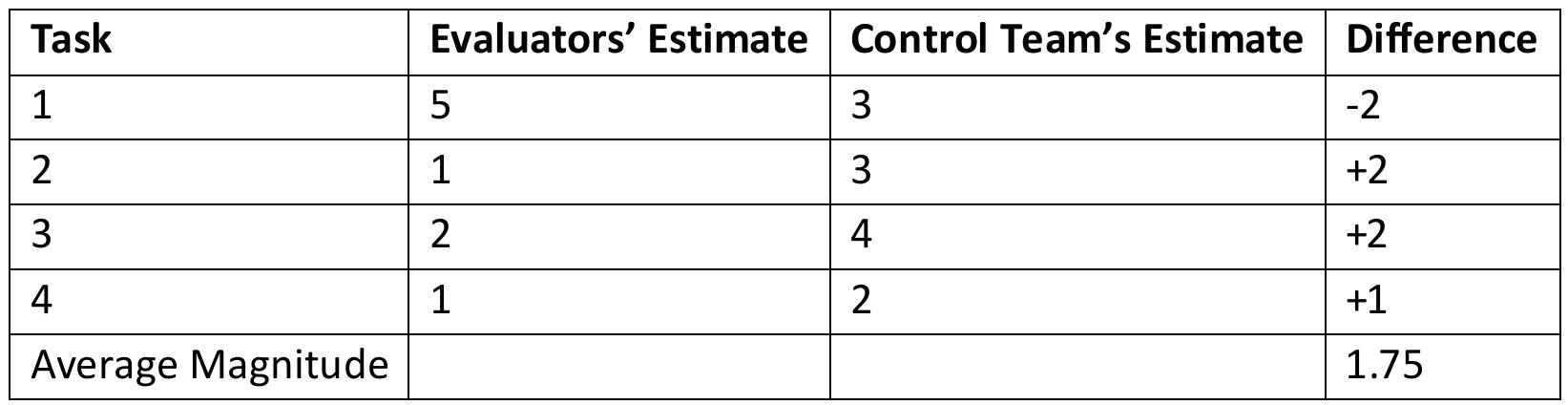
![Table 8.7: Issues Found in Reviews The number of patterns identified is consistent with patterns found in other systems (see [62].) Since patterns provide ready-made documentation, they are useful during the review. However, the number of patterns is not expected to be correlated with the number of issues identified; indeed, a simple inspection of the data indicates it is not.](https://figures.academia-assets.com/120841515/table_045.jpg)